UPDATE: With new sources coming in about the virus, including some from Kapersky Lab’s latest article, we want to let our readers know that Petya/NotPetya/PetrWrap is a Wiper virus that’s solely meant to destroy data on a PC, not a Ransomware.
On June 27th, 2017, Ukraine grounded to a halt by a vicious cyber attack which created chaos around most parts of Europe and the USA.
Within 24 hours, over 300,000 computers in over 25 countries got infected by a malware that’s known by a few names, but is commonly known as ‘Petya’.
What Petya is and How it Works
Like your average ransomware, Petya blocks access to certain files on a computer that operates on Microsoft Windows and encrypts them.
The virus would crash the PC and show a stop error, also known as the Blue Screen of Death (BsoD). Afterwards, the PC would restart but prevent the operating system from loading by altering the hard drive’s master boot record (MRB). The user would be kept on the MS-DOS prompt that would also act at the ransom note. The only way the user would be able to retrieve their files is to decrypt them with a key that’d be provided by the perpetrator(s), who would demand a ransom fee in Bitcoins in exchange.
If the victim doesn’t pay the ransom, they would have to face losing all of their files, just like the victims of the WannaCry/WannaCrypt ransomware. And like the victims of WannaCry, the victims of Petya are ordered to pay out a sum of $300 in Bitcoin currency and send it to a given Bitcoin address.
How the Petya Strand Spread Across the Globe
There are theories that the popular Ukrainian Accounting software, MeDoc, was hacked before the use of the automatic update feature was ready for users to download the malware onto every computer that uses the software; all while using the EternalBlue backdoor exploit.
Eventhough MeDoc hasn’t been classified as the original source of the Petya ransomware, and that the company itself deny being that source, the evidence that is present points the finger at them.
Symantec analysts have confirmed #Petya #ransomware, like #WannaCry, is using #EternalBlue exploit to spread
— Security Response (@threatintel) 27 de junio de 2017
Minutes after it was executed, the worm spread across government institutions, banks, and even the Chernobyl nuclear facility. It then travelled overseas, hitting other European countries such as Germany, Spain, France, Russia, and the UK. Some of the companies affected include Rosneft, Saint-Gobain, WPP, Deutsche Post, and Mondelez International.
The latest companies that have fallen victim to Petya are Merck and DLA Piper, an American pharmaceutical company and a multinational law firm located in the USA. Merck is known to be one of the largest pharmaceutical companies in the world.
Open Data Security has been keeping up to date on the ransomware’s movements, how many other countries/companies have been infected by it, and how many transactions have been made to the malicious hackers behind the Petya strand.
Since the outbreak, 43 transactions have been made to the bitcoin address, bringing the current total sum of 3.87408155 BTC. That’s the equivalent of approximately $9734, £7591, or €8565.
?? 27 payments have been made since our last post. Bringing a total of 40 transactions, and 3.64053686 BTC.#petya #ransomware #cyberattack pic.twitter.com/0czGhMyOxm
— Open Data Security (@ODSops) 28 de junio de 2017
At this moment in time, the bitcoin address hasn’t been disabled, and payments are still being made to it.
The Difference Between Petya and WannaCry
Petya has the same cybernetic traits as WannaCry does, but excels in network speed over WannaCry, which is the reason why the malware spread between continents so quickly. Unlike WannaCry, which only disables access to certain files, the strand encrypts the entire hard drive from usage . This makes your computer completely useless and inert until the infection is removed.
Additionally, IT experts stated that Petya’s code quality ‘improves from iteration to iteration.’ There is no kill switch that could slow the ransomware down, and the Petya strand can affect PC’s that aren’t secured against EternalBlue, and can also deploy other actions. For example, lacing Microsoft Word documents with malicious macros, and embedding the worm in software update features, which MeDoc, unfortunately, fell victim to.
What to do when you’ve executed a file containing Petya
Currently, there is no method to decrypt information on an infected PC, but there is a way to stop the encryption before it gets infected. If you get presented with a prompt on your monitor or laptop screen like this, shut down your PC immediately. Shutting down your computer will stop the encryption process.
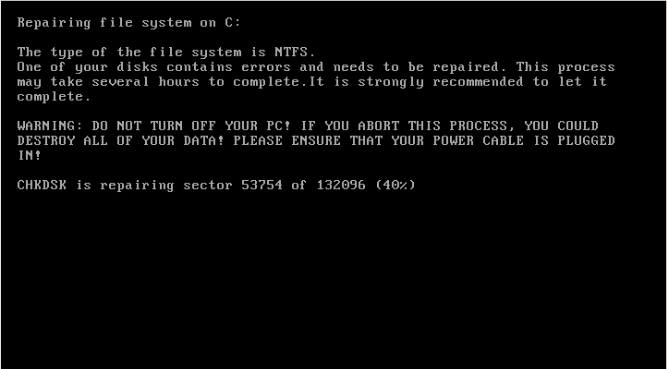
Next, boot your operating system with a recovery disk like LiveCD. Then, scan for ‘Petya.A/NotPetya’ and remove it. Don’t forget to copy your files to a safe location, so you won’t face the threat of losing your data.
Many other experts are currently obtaining samples of the Petya strand, and are looking for ways to block the ransomware’s distribution.
Petya Warnings from Open Data Security
We want to provide you with some very important warnings if you’re operating on Microsoft Windows, so you won’t become one of Petya’s victim:
Back up your system’s files in a safe destination and keep it offline.
Make sure that you have the latest Microsoft Security Patch install on your PC.
Check that you have the latest version of a reliable anti-virus software on your PC
Don’t click on attachments from unknown sources.
If you see an email telling you to click on a suspicious link, delete the email immediately.
If your PC is infected by Petya, DO NOT MAKE ANY BITCOIN TRANSACTIONS TO THE EMAIL ADDRESS IN THE PROMPT.
Sources are coming in that the hacker’s email address is currently disabled and won’t be able to receive any emails or payments sent to them. Therefore,you won’t be able to gain access to your PC even with a Bitcoin transaction.
If you urgently need advice, require an anti-ransomware tool, or fear that you and your company may be under threat of a breach, contact Open Data Security immediately and we will be able to help you with any queries that you may have.
Further updates will be posted on our site, but in the mean time, you can hear the latest about Petya by following us on Twitter.







Comments are closed.