You only need a few moments to upload information on the Internet, and it will be public forever. Nowadays, we are facing a dilemma: to keep our personal data safe, while building a personal digital brand or being a visible part of a business.
This situation is tough. It is not surprising when you find employees and managers who publish sensitive data on the Internet, and this data can damage their company. Doxing is about gathering this kind of information, and when you know what hackers can do with it, then you will see the digital world with new eyes.
What is doxing?
Doxing is based on gathering information on the Internet of people and companies. The word comes from “docs” (documents). There is no need to know a lot about code or computers to perform doxing, but it could be complicated if it is performed by computer analysts.
This technique is used by some journalists during their research activity, but also by governments or security forces when they investigate computer crime. As Chema Alonso says (one of the most famous computer analysts in Spain), doxing is also used to reveal hidden identities on the Internet.
Doxing requires good intuition, but also knowing how to use tools that are available to track information. Part of that information is found on open data sources like the WHOIS protocol (if it is public, then you can check the information about the ownership of a domain name) and on social networks like Facebook. Also, there is information on the documents which hackers or organisations like Anonymous had leaked after their attacks.
Google is another popular way to look for personal data. You only need to type the email or the complete name of the person you are researching.
Is doxing illegal?
Firstly, it is not illegal to gather information that is on the Internet, even if it is private. Many times, users are reckless, and they post their personal data on websites, such as email, phone number or address, among others.
However, a person who performs doxing can also take advantage of illegal acts. This happens when hackers attack companies or public organisations, and they publish the documents and data they had obtained after the hit.
Sometimes, it is very easy to access that information. For example, in October and November of 2010, Wikileaks leaked documents about the Iraq War and the foreign policy of the United States. That is why, at that moment, the public were discussing if Wikileaks was making more harm than good by disclosing sensitive data as the organisation was putting lives at risk.
However, some cybercriminals publish on the deep web the information they had stolen, then for everyone else, it is more difficult obtaining that information.
After all, doxing is legal in countries like Spain, but in some others like the United Kingdom it is considered an illegal activity. The Crown Prosecution Service considered doxing a criminal offence like cyberbulling or creating a hashtag to encourage harassment of victims.
How can you avoid doxing?
On one side, you have to be very careful with the information you share on the Internet. If you have a blog or profiles on social networks, hackers can gather data about you. So, it is recommended to take care of the kind of information you share to avoid an embarrassing situation.
For example, you may find people who leave a comment on a blog with their personal email. Hackers or any person with bad intentions can see this and look for the personal profile on Facebook. If these people use the same email for other online services, then hackers will gather information about them without effort.
On the other side, you can’t avoid some situations like businesses data theft. The Ashley Madison case was very visible, it was a difficult situation for the clients of this social network because of the nature of the revelation, but also, because hackers published all the sensitive data they had stolen.
That is why it is recommended to create different email accounts to sign up for online services such as social networks or e-commerce. When you have other e-mails, you can use your email work only for labour issues, and your personal email for personal stuff.
Moreover, if you are a client of a company which has been hit by hackers, then you should change the access credentials and be aware of the kind of information the hackers got from you. After the attack, you might receive a phishing email, so you need to look at each email with caution.
Should business worry about doxing?
Doxing and social engineering are linked. As we saw in this post, social engineering can be very dangerous for companies, that is why businesses of all sizes need to worry about doxing.
When it comes to the cybersecurity of a company, the social engineering shows us an important lesson to prevent doxing: the human being is the weakest link. In other words, for hackers, the human factor is the main vulnerability of a company.
Cybercriminals will gather information about workers, and this data might be useful for hackers at the time they want to attack a company. Down below, you have a clear example of how the hackers could work in this situation:
Imagine that there is a hacker who wants to attack a business. Firstly, they will search for relevant information on the business website. There, they may not find anything important, nor an About us page. So, it might mean that the company is not interested in showing who is working there.
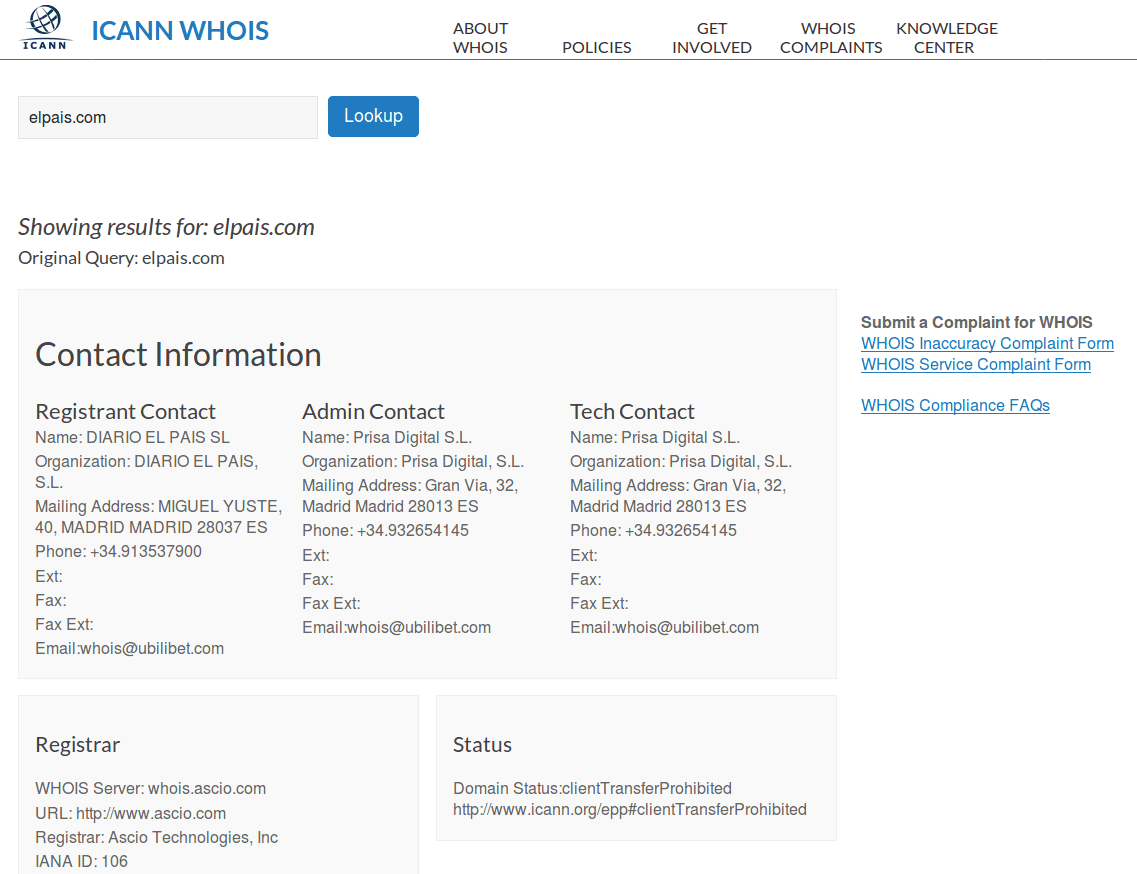
Doxing starts when the hacker checks the WHOIS of the company’s domain. If the WHOIS is public, the hacker can gather sensitive data like an e-mail, an address, a telephone number, the owner of the domain, the server name and the DNS.
Now that the hacker knows the name of the owner of the domain, they will type this name on Google combined with the company’s name and the area it is located. Then, they may find a LinkedIn profile and see who works at the company, as this social network shows links between people.
All this information gathered by doxing is useful to prepare a phishing attack. The hacker can send an email to a worker of the company, introducing themselves as a member of the technical support of the company’s server. They may ask for the access credentials by saying that there is a technical problem on the server. This kind of attack is very common, but the hackers are always innovating.
In this example, we learned that if you buy a private WHOIS, your sensitive data will be safer, but another lesson is that companies need to invest in cybersecurity, as their employees need to train on how phishing attacks work, and what information they can share on the Internet, and what they can’t. Finally, this is how businesses can avoid damage by doxing.
- The keys to get the ISO 27001 certification - November 14, 2019
- Managed Security Service – MSSP - October 23, 2019
- DDoS Attacks – An In-Depth Guide - September 12, 2019








Comments are closed.