Most people and businesses tend to assume that they will know if their accounts or network has been hacked. They might have sophisticated systems in place to prevent hacking or cyber attacks, and so believe that an attack will be obvious if it does manage to get through.
The problem is that sometimes your computer could be infected and you won’t know a thing about it the moment it happens. In some cases, days, weeks, or months might pass before you come to realise that your computer is infected. Meanwhile, your computer has effectively become a zombie, spreading the infection to other devices on your network or even those you share a connection with.
Often when the hack is discovered, the damage has already been done. Malware makes it difficult to know just what your computer has done in zombie mode, and so you need to find an effective way to deal with malware and reduce the risks of your devices becoming infected.
What is malware?
There are so many different types of different online threats that businesses need to be on the look out for. Everything from keyloggers and phishing to trojans and ransomware. You may have recently heard about the WannaCry ransomware which hit a number of medium and large-sized companies all over the world. These are the types of threats businesses need to know about.
For businesses, many consider malware to be among the most dangerous. Malware stands for malicious software, and it is thought to be incredibly threatening because it intends to access a device without alerting the user. You could have malware on your device right now and you wouldn’t know about it. They are coded to ensure that they stay hidden, as the longer they are hidden on your device, the more damage they can do.
There are many different virus that fall under the category of malware
Avast explains that there are some telltale signs to alert users if their device has been infected with malware, such as “pop-ups, spam, and frequent crashes”. You might also find that your computer is running a lot slower than usual, which is why many suggest malware turns your computer into a zombie.
Your computer could be used to send the malware out to others through spam, and because your computer is occupied with something else, it can really slow your device down. This can hugely impact worker productivity, as they cannot get things done at their usual pace. It is a challenge for many businesses because they do not have the right protection in place!
A lot of the time, businesses expect an anti-virus to take care of it. Often though, you’ll need to take further steps to prevent malware getting in. Anti-viruses can be useful to help to keep your network secure, but it may not be enough. You’ll need to really look into your network security in order to make sure it is as good as it can be.
Defining malware is difficult. There are a number of different ways they can infect your device, and there are many different types of malware. For businesses it is important to understand what risks you face and where they come from so that you can better educate your staff on security.
Adware
Most people are at least familiar with adware. The majority of the time, you will find that it is simply frustrating and irritating to you, but it can sometimes pose a security risk to your network and your devices if you do not deal with it properly.
When you have adware on your device, or even on a website you use, you will find that a number of intrusive advertisements will pop up. It can be a bother to deal with, but adware can hide more malicious spyware which will track your activities and share it with third parties.
The classic adware you’ll encounter is advert after advert, all popping up in quick succession. Sometimes even the act of closing one can trigger another pop-up, which might not seem so bad. However, your device will be trying to load all of these advertisements, which can really slow down your computer’s performance and take processing power away from where you need it most.
Usually closing the source of these apps is enough to stop them, but as we can see from the persistent adware on the Google Play Store, even that isn’t enough. The apps will continue to appear even after you close it, and so the only thing you can do is remove the app completely from your device and use anti-malware to get rid of any traces.
Apple devices aren’t safe either, as Chris Barylick tells us that there have been “nearly 250,000 new instances of macOS malware in the first quarter of 2017”. This could be a real concern for businesses using Apple products, and so it is important to take steps to prevent adware from infecting your device.
Sometimes, adware bleeds over into spyware. Spyware is just what it sounds like: malware intended to spy on the user. It will follow your activities online in order to provide advertisements based off of your interests, in order to try and get you to click on the advert and be taken to a malicious website.
Bots
Another type of malware that you may encounter is the bot. Bots are software programs which have been created with the intent to automatically perform certain actions without the user’s knowledge. While some are innocent enough with their intent, such as bidding on internet auctions, there are more malicious ones out there that you need to be cautious of.
wiseGeek explains to us that botnets are basically a number of infected computers using remote-controlled software for the benefit of a single hacker. This means that bots can be used to launch DDoS attacks, send out spam, or even send out more malware to any devices connected on the network. This means that your device could be used to spread more malware quickly, causing it to slow down dramatically and reduce the productivity of your works, as the CPU is occupied with the spam and not what your staff are working on.
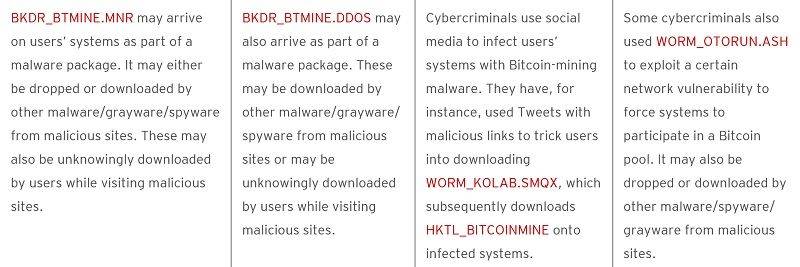
These are examples of the ways that cyber criminals can get botnets onto your devices
This type of malware, as TrendMicro tells us, can get onto your devices in a number of different ways. However, they tend to “arrive via malicious downloads or through social media”. On social media sites, especially ones like Twitter where every character counts, shortening the URL makes it difficult to verify the source as safe. Even if you trust the user it is important to check the link is safe… but when the link has been shortened you cannot do this. And this is how a lot of bots get into your system. But there are also many other methods, as TrendMicro explains below:
One example of a botnet being used maliciously by hackers for the purposes of cyber crime comes in the form of Bitcoin mining modules. Bitcoin mining allows users to generate more Bitcoins for the market, but it is a very intensive activity for a computer to run. Hackers have now created botnets to help them profit from it.
Although there have been reports to suggest that profiting from Bitcoins in this way is not very effective, it can still cause a lot of harm to your computer. Bitcoin mining is a huge drain on your CPU, meaning that getting your computer to run as it would normally isn’t going to happen. For businesses this means that workers cannot do their job, and so productivity will suffer. Cyber attacks like this can cost your business more than just money.
Preventing your computer from becoming a zombie
There are many different types of malware out there that could cost your business a lot, and not just in terms of money. Even adware can do damage to your business, as it can slow devices and reduce productivity massively. It is a huge drain on your computer performance and will turn your device into a zombie, spreading the infection and forcing you to slowly shamble through your work day.
So how can you prevent this from happening to your business? To start with, you need to ensure that your employees know the basics of security. By teaching them to question everything they see, you are going to help to protect your business. They will view emails with more caution and avoid clicking links that could cause harm to your business.
We have been told to expect more cyber attacks in the future, and so properly securing your business is an essential. Open Data Security can help with that, so why not contact us to see how we can help you defend against malware and keep your business safe?
- Why you need to train your CEO before your employees - September 14, 2017
- Your computer may be a zombie! - July 25, 2017
- All You Need To Know About GDPR - July 4, 2017






Comments are closed.