Probably, the name of John McAfee is familiar to you. McAfee is the founder of the antivirus which bears his name. At the end of 2012, McAfee was wanted because of the murder of his neighbour, Gregory Viant Faull. From the beginning, this event received a lot of media attention. McAfee escaped to Guatemala and came into that country illegally because he was investigated by the U.S. justice.
During his time on the run, McAfee claimed his innocence through his Twitter account and his blog. However, something happened before the police discovered where he was.
On 3 December of 2012, the Vice website published an exclusive with a defiant headline: “We are with John Mcafee right now, suckers“. In the post, there was a picture of McAfee with the chief editor, Rocco Castoro. It didn’t take too long to know where they were:

What is the metadata of a picture?
Every time you take a picture with a device (it may be a smartphone, a tablet or a digital camera), the file contains information (metadata) such as the date and time of its creation, model of the device, version of the system operator, image parameters (exposure time, iris aperture, focal length…).
If the smartphone’s geolocation is not disabled, or your digital camera has GPS, the metadata of pictures will disclose where they have been shot.
This information is organised according to a standard called EXIF (Exchangeable Image Format), which provides information to some file formats like JPG, TIFF, RIFF and WAVE. The following image shows how you would see the metadata of Vice’s picture with John McAfee:
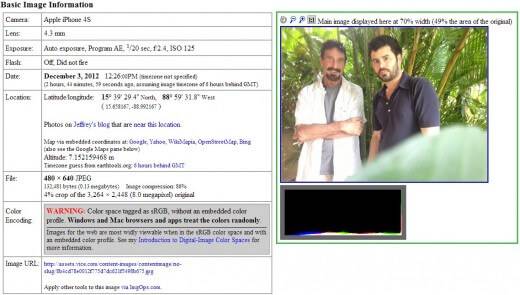
To know the metadata of a picture, you just need tools like EXIFTool, one of the most popular when you want to remove metadata or even delete it from pictures.
This tool would be useful for Vice or even for John McAfee, as ironically his company revolutionised the computer industry. However, you may wonder if you need to take steps to prevent private data leakage.
Metadata and social networks
There is no room for doubt that social networks are the most popular places when it comes to publishing pictures. Metadata processing is a privacy issue, and every social network has their way of management. Some of them delete information, some others keep it. Let’s see the metadata processing and privacy of the most popular social networks: Facebook, Twitter and Instagram.
If you upload a picture to Facebook servers, copy the image’s link and paste it in this online tool,you will see that Facebook does not keep the metadata in pictures published on this social network. The next image shows the metadata that you can extract from a picture uploaded on Facebook:
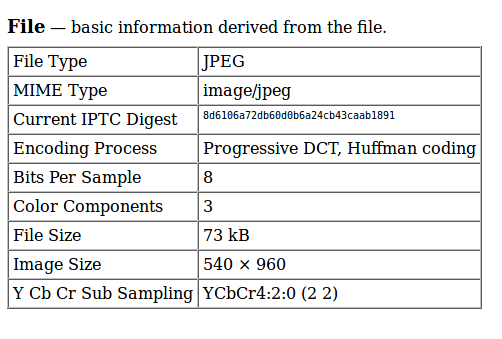
However, Facebook’s Privacy Policy informs users that Facebook gathers information from the content which users share. They want to know where and when you have taken your pictures. They also say that this information is useful to improve their services and develop others.
With the same tool, we check if Twitter deletes the metadata of its pictures and discover that they do. To know this, it is necessary to upload an image from the web application and also from the mobile application. From its Privacy Policy, Twitter explains that they gather a huge amount of information about their users, and they took that information from the content which users share.
In the case of Instagram, you can not check metadata images as this social network does not allow you to download pictures, or copy an image link from the desktop version.
In essence, the social networks mentioned protect users from information leakage, but not all of them do this (like Google+, Flickr or Tumblr). It happens the same when you upload pictures to cloud services like Google Drive or Dropbox. That is because files are not modified on these applications, and anyone who can access them could also read metadata.
Could metadata put your company at risk?
At this point, you need to know that metadata is in all kind of digital files, not only in digital pictures. Text documents, PDFs, and video metadata which might be disclosed or changed by some tools that are easy find on the Internet.
Some companies do not have any problems sharing their location, or letting people know about the machines they work with, as metadata shows the device you used to take a picture. However, other companies, and even freelancers, prefer to control everything they publish about their professional activity. That is the best you can do, as hack methods change constantly.
There is an example which explains how a single picture might damage the brand image of a company or a freelancer. Let’s say that a hacker wants to do some social engineering with some employees of your company. They might gather information about your business, and the metadata they may find in your files might give them clues.
A hacker may send an e-mail to your employees saying that they are part of the technical service of your digital camera. Finally, they might ask you to click a link with malware.
Situations like this one happen every day. That is why computer security training needs to be vital for companies and digital nomads. The ODS team customise your training according to your business activity. There are cyberattacks every day, and we will work on your security so you can avoid being the next hacker victim.
- The keys to get the ISO 27001 certification - November 14, 2019
- Managed Security Service – MSSP - October 23, 2019
- DDoS Attacks – An In-Depth Guide - September 12, 2019








Comments are closed.