Metadata is data which provides information about other data. It is information that describes content. In the computer field, searching and storing information is easy thanks to metadata. All kinds of digital files contain metadata: an image, a video, a song, a PDF file or a Word document, among others…
Even a link has metadata. It is also known as “social metadata”, as when you share a link on social networks, you see a preview which is the metadata of that link (title, image and description). That information is previously written in the source code of a website.
In short, any file has metadata from its creation, but it can be manipulated or deleted with specific software. You can discover more about how to read and delete metadata on pictures on this post.
Information is one of the most valuable things on the Internet, but metadata is not well known among people. On one side, the majority of users create and share content without knowing that they contain metadata. Data brokers take advantage of users activity on the Internet, as they gather metadata from the content they share.
On the other hand, metadata might be dangerous for businesses and organisations, as workers are always the weak link. They might hand out sensitive information with their devices.
There are not many famous cases about abuse of the privacy because of metadata, as most of them are very technical. This post is an introduction of this topic, so we are going to see some of the cases when metadata caused a breach of privacy.
Metadata in calls
It was October of 2013 when metadata started to sound familiar to people. Because of the documents leaked by Edward Snowden, ex-NSA contractor, people knew that their privacy was infringed through their calls by the U.S government.
The then U.S President, Barack Obama, tried to justify the activities of the NSA. He quoted article 215 of the Patriot Act which said that “the government is allowed to obtain information from third parties” to gather data related to terrorism.
Obama explained that “when it comes to telephone calls, nobody is listening, as the software does not work like this”, but it selects calls through metadata.
In the beginning, it was assumed that those who spied calls of people didn’t know their names, or what they talked about. However, they gathered telephone numbers and the duration of the calls.
With the Snowden case, the U.S government talked about metadata like it was minor information. However, the truth is that sometimes it may reveal more than the content.
Metadata in emails
In the midst of the Snowden documents scandal and the disclosure of the PRIMS Program of the NSA, The Massachusetts Institute of Technology (MIT) published an application called Immersion. It is a tool where users can login with their Gmail or Yahoo accounts to obtain maps and graphics that show contacts they are in touch with. Immersion also shows how many incoming and outgoing emails users have or their new contacts over time.
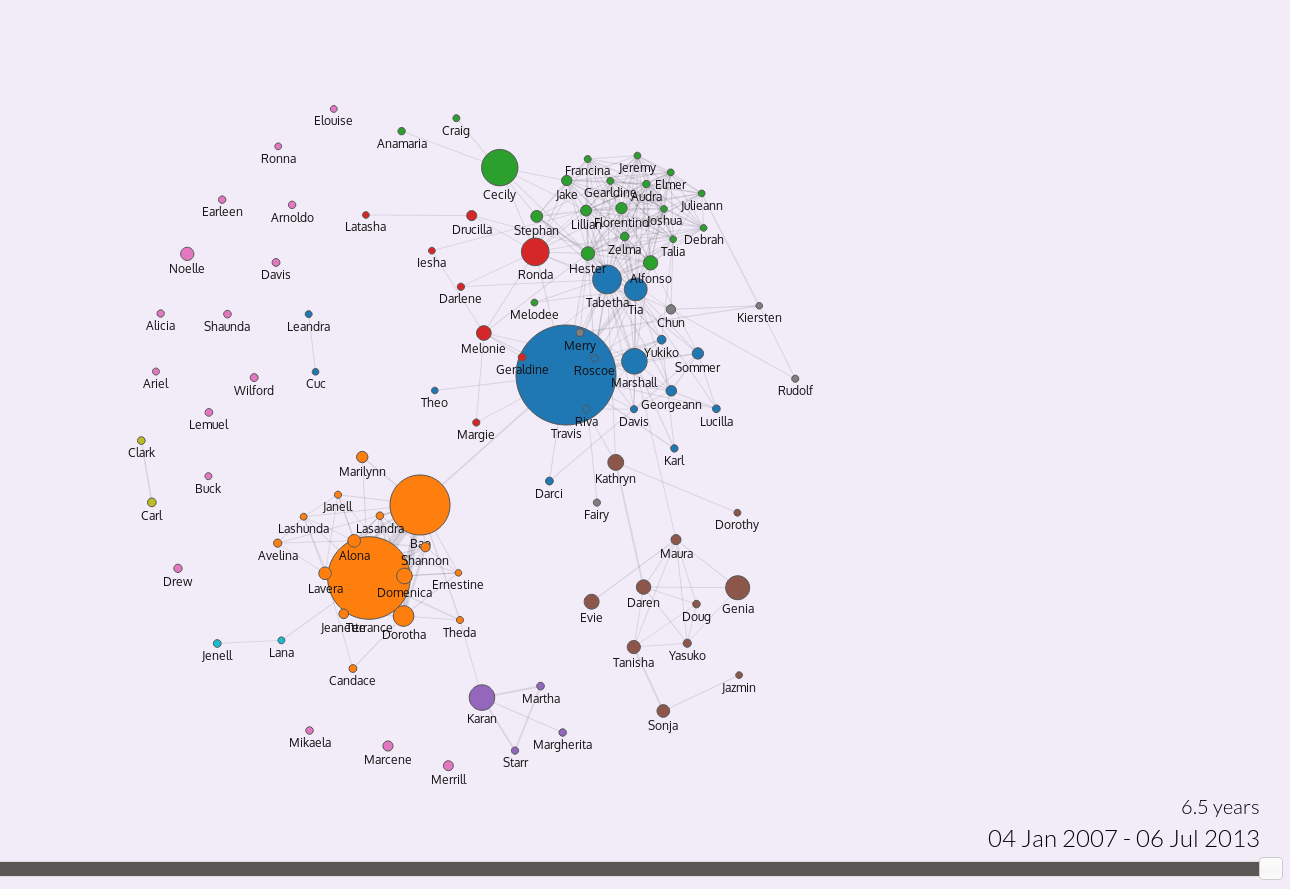
Screenshot of the Immersion’s demo. It is a map made by the metadata extracted from a user email account.
In other words, Immersion shows that metadata reveals private information which might be important to protect users privacy, and the tool does not need to analyse the content of emails to gather that information.
This idea was not new. There were people who said that metadata is important. “They say that it is just metadata (…)” but metadata reveals “who you are talking to, when you are talking to them, where you travel”. These are statements by Edward Snowden at his TED Talk.
Alt: He did his talk through a monitor, as he started his exile after being charged with high treason.
This situation was promoted by the U.S government, apparently, without the permission of other nations. So, you might wonder if it is worth worrying about metadata records or if there are more organisations which record and store metadata massively. Could metadata impact on a visible leader of an organisation?
What can they do with the metadata of a citizen?
It was 2009 when a German political called Malte Spitz wanted the data that his telecommunication provider, Deutsche Telekom, gathered from him as a client.
Spitz appealed to the Data Protection Directive of the European Union which was a response to the security problems after the 11M attack in Madrid and the 7J in London. The regulation forced telecommunication providers to store metadata of their clients over a minimum of six months until two years. Later, in 2014, the European Union Court of Justice overrode that regulation as it was an interference in privacy rights of citizens.
However, Spitz went to German law several times because Deutsche Telekom did not want to provide him with the data they had about Spitz and which was gathered through his smartphone. Finally, the justice ordered Deutsche Telekom to give Spitz his metadata of the last six months.
It was a huge amount of information, so Spitz asked for the help of the journalists at Zeit Online. They created an interactive map with lots of details about Spitz’s life: where he went during the day; where he lived or worked; who called him and who he called; how long the calls lasted and the telephone number of his contacts. All these thanks to the metadata registered by Deutsche Telekom.
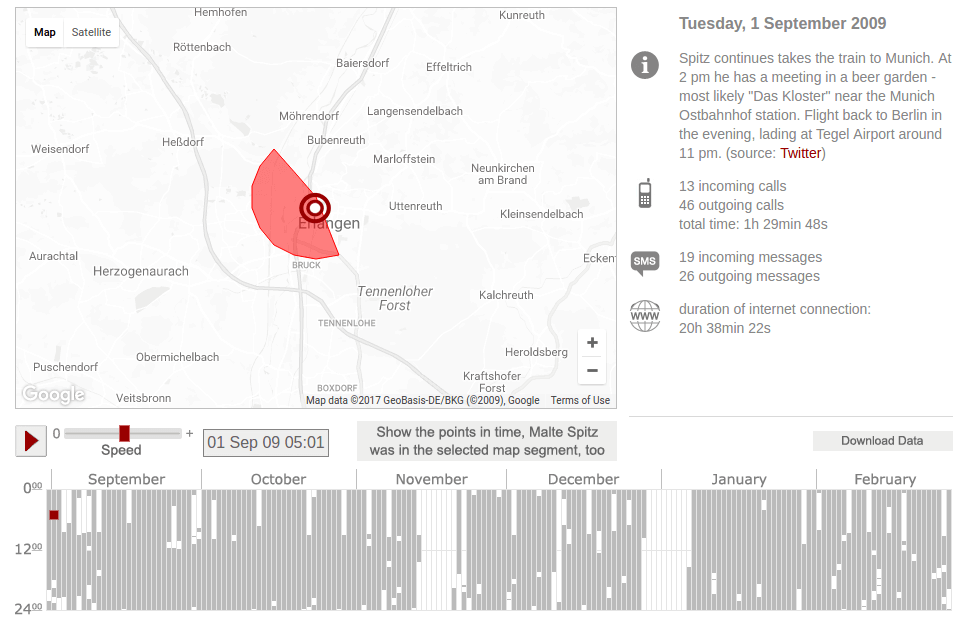
In the website, you can see Spitz’s movements and activities over the six months.
Spitz proved that metadata records were interfering with the privacy of citizens, and this is something that the European Union Court of Justice decided years later.
There is an important detail behind this story: Spitz is a politician from the Green Party in Germany. Depending on who is managing that metadata, Spitz’s information might be used to favour interests of third parties.
When openness is a problem
Data publishing (which contains metadata) combined with the growth of processes that citizens can do online might be the best combination to hack an identity.
In July, the Stockholm Justice declared the insolvency of the executive director of Securitas company: Alf Goransson. It was an unknown process for Goransson until he received the notification.
Everything started when a hacker took advantage of openness and digitalisation of public documents in Sweden. He stole Goransson’s online identity and took out a loan. The loan amount is unknown. However, the Swedish justice made that decision which was appealed by the executive.
At present, Goransson is not working anymore with some organisations where he was a member, at least, until the embargo is lifted. This situation might affect Securitas in some ways like its profits or damaging its brand name.
According to Bloomberg, so far this year 12,800 online identities were hacked only in Sweden, a pioneer country in openness issues. However, this case showed us that a bit of suspicion is needed and social engineering can ruin someone’s life.
When a business reveals more than it wants
When it comes to managing a device, two security problems might appear:
- Information created by companies and individuals is undervalued.
- People used to think that they needed enemies to worry
Industrial espionage used to be the most obvious reason for organisations to worry about their information and metadata. Those organisations have competitors which want to know products or services which they are working on and the next steps they are taking in the market.
We need to think that in all companies there are humans who work with sensitive information through their devices. Information has metadata, and it might reveal things that almost nobody wants to.
Open Data Security is creating a tool to delete metadata from the content of organisations and companies which need to share documents with third parties or even publish it. Shortly, we will bring you more information about this new resource which is going to be designed for those who wants to protect their privacy and their client’s data, too.
Information is the tradeable currency on the Internet. You need to place value on the content you create, as it says more things about you than you think.
- The keys to get the ISO 27001 certification - November 14, 2019
- Managed Security Service – MSSP - October 23, 2019
- DDoS Attacks – An In-Depth Guide - September 12, 2019








Comments are closed.