Wake up and look at the phone. Have a shower, get dressed and close the door when leaving your house. Get in the car, put on the seat belt and drive to work.
It is not until you have your very first coffee, when you realise you have been acting on autopilot mode. Without thinking.
It is logical to close the house door; we assume that for safety you have to put on your seat belt when getting in the car. We know that using a helmet when riding a motorcycle protects us, and for the same reason, we try to look before crossing the street.
We integrate these actions in order to survive the dangers of real life. But the question is: are we prepared to survive in the online world?
While reading this, you are one of the 3,764 million people connected to the Internet. You are part of that exorbitant amount of users in the network that generate information every time you:
- Connect to a wifi network.
- Do a search on Google or any other search engine.
- Click on a link.
- Register in a web or application.
- Download and install an application on your device.
- Send or receive an e-mail or an instant message.
- Buy something in an online store.
- Like a publication on social networks.
- Publish content on a social network, blog, application or web.
And the list does not end here. It is much longer because we are doing more and more things from our Internet-connected devices. That’s why we produce much more information than we can imagine.
Data speaks for itself: the amount of information we generate about us is immense and users underestimate not only the quantity, but also their value. So the question becomes inevitable:
Why should we be concerned about the information we generate on the Internet? Even if you don’t believe so, there are people and entities that want that information, that are willing to pay for it or to obtain it using methods of doubtful ethics.
Companies, organisations, governments … Our data is gold and from the moment we own an electronic device connected to the Internet, we start living in glass houses. The ones who are able to see through that glass and are aware of those facts, are commonly known as hackers.</p
Hackers, the bad guys of the oasis

“Hacker” is a widely used term today. Its meaning may vary according to the context in which it is used.
For example, the first meaning that appears in the dictionary of hackers, points out that it is “the person who likes to investigate the intricacies of programmable systems and how to squeeze their capabilities, unlike the majority of users who prefer to learn the minimum.”
That definition does not speak of someone who commits criminal acts on the network. However, through the literature that has emerged around the Internet and the media, you can easily verify that “hacker” is the most common way of referring to cybercriminals. Individuals who are also known as “black hat” hackers, “crackers” or simply “attackers”.
The main objective of a cybercriminal is usually to earn money. We say this because there are also cases in which the motivations may be ideological (hacktivism), or the intention may simply be to boast of what one is capable of doing.
What matters to users is cybercriminals design complex attack methods every day to obtain sensitive information about us. And they get it. Of course they do.
According to the data, we are talking about the criminal activity that generates the most money in the world. In fact, in a recent report by the Accenture consultancy, it is pointed out that a cyberattack can have higher costs than a natural disaster.
Attack techniques with which they get what they want

The danger on the Internet exists for absolutely everyone. In cybersecurity, it is often said that zero risk does not exist. For that reason, we should not stop trying to protect ourselves.
The attacks we will see below are the most common ones, those that generate the most headlines, and to complicate this situation even more, the way in which they can be presented can be very varied.
That is why it is so important to know what we are facing, as well as knowing the way in which the attackers act and the way in which we can prevent ourselves from being victims of a cyberattack.
Phishing or identity theft
Source: Symantec 2017 Internet Threats Report
It is the most common scam on the Internet. It is based on posing as a person of trust or in a company of which we are customers to obtain our data: passwords, banking information, among others.
To do this, the cybercriminal uses social engineering to make the deception credible. This means they design and send very similar corporate e-mails to those customers who usually receive these kind of emails.
In a phishing email, they usually ask for one of these three actions:
- To answer the e-mail by providing user information.
- To download an attached file in the email which contains a virus.
- To click on a link that leads to a fraudulent web page in which the attacker can ask for other actions such as putting personal data that will be used by the attackers.
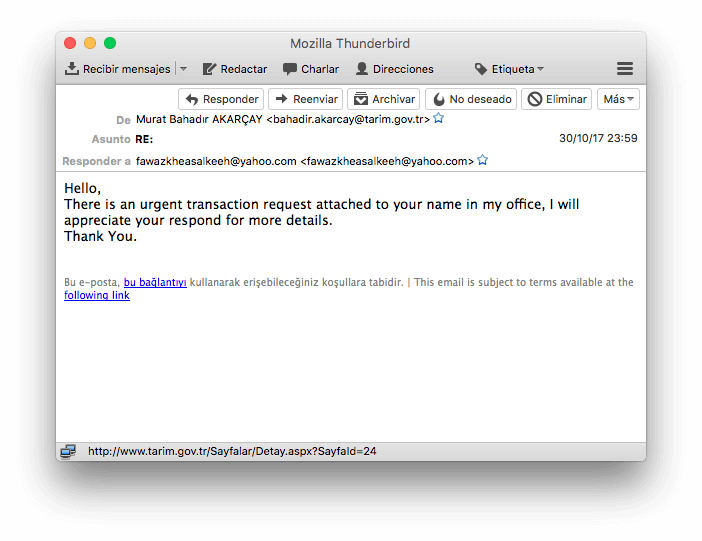
Screenshot of a phishing email requesting the download of an attachment. In it you can see a strange email address and there’s no return address.
Phishing attack scenarios are not limited to email. It is possible to be attacked by instant messaging or by phone calls if you pose as a trusted person.
Phishing is also present in fraudulent websites you can access because they have managed to appear in Google results or because they are in the profile of a user of a social network.
For all the above, the best prevention for phishing is based on distrusting the content we receive through e-mail, instant messaging, social networks and even distrust when someone calls us to ask for private information over the phone.
There are also antivirus and tools that scan the attachments of our emails or block potentially damaging links. These are recommended and valid solutions, but not as effective as caution.
Ransomware, the worm that blocks access to your computer
Source: Barkly.com
It is the most feared virus of recent times. The ransomware has been the protagonist of many headlines for affecting users, companies and institutions around the world. Its modus operandi is to infect devices by blocking their access and asking for a ransom in exchange for returning things to normality.
Some variants of ransomware also encrypt the information we have in our devices. In these situations a reverse of that encryption should be performed.
The most important thing we should know about a ransomware is that you should not pay the ransom the attackers request. The reason is that there is no guarantee we will recover our information, so paying could involve not only the loss of data, but also money.

Screenshot of a ransomware in which the FBI logo appeared to demand the rescue of $200 from those affected.
The way in which this virus enters our systems is also diverse. It can be through fishing: a message in which we are asked to download a malign file or program.
It is possible for ransomware to infect computers and infrastructures by exploiting vulnerabilities in the system or an application installed on it. The possibilities are as complex as they are diverse.
So how should we prevent a ransomware from attacking us? The truth is that it is difficult, since new variants are emerging every day. Therefore, it is best to have the backup copies of your files updated so that we can restore it in case our equipment is blocked and the information is encrypted.
Distributed Denial of Service Attack (DDoS)
Source: Quarterly Report on Malware of Securelist 2017
Every time we visit a web page, a request is made to a server, so that it responds with the data (web page) to which we want to enter.
Imagine for a moment many requests are made at the same time, so many that the server is not able to stand and stops providing a service, so you can not access the web page.
This is what is intended to be achieved with a DDoS (Denial of Service) attack, in which a saturation is achieved by overloading the servers from a single machine, whereas in a DDoS attack (Distributed Denial of Service), the attack comes from several points such as a network of bots (machines).
As users, the only thing that can be done when you can not access a web page or application that might be suffering from this type of attack is to wait for normality to be reestablished.
Exploiting vulnerabilities and errors
It is usual that we have to update our devices every time a new version of the operating system or the applications we have installed is released. Many times, this happens because they bring news, such as new functions.
Sometimes, what they do is solve a security breach that could compromise the information of the users. That’s why is is important to keep the latest updates.
Occasionally, the security breaches of a system are not fixed until attacks are already occurring. Therefore, most of the time we are not aware of when they have attacked us and a long time passes until we find out. A time in which attackers take advantage to extract private information from users.
What harm could a cyberattack cause us?

As we said at the beginning, the main objective of cybercriminals is to earn money. Therefore, when they steal information from us through a computer attack, their next step is to sell it on the black market or take advantage of it.
Any sensitive data can be very precious, from the content we keep in our email, to our computer or mobile phone; logically, e-mail addresses, bank and credit card information are also of great value.
And the way in which cybercriminals do business does not end there. We can also filter applications that directly take money from bank accounts. Android.Fakebank is one of them. The Trojan infected Android devices mainly from South Korea and Russia during the summer of 2016, according to Symantec.
It was installed through an application that apparently seemed to be Google. Once installed, it worked in the background and stole banking information from the user.
To make things worse, when he realized there were strange transactions in his bank account, the Trojan blocked any bank call made from the infected device.
This made the user take longer to block the activity of his account, and therefore, gave advantage to cybercriminals to extract more money. The result is to be expected: a bad experience ending up as a looting.
This is another example of the risks users run from the moment we have in our hands a device with an Internet connection. Now, each problem has a solution, but that is something we will raise in the next article.
- The keys to get the ISO 27001 certification - November 14, 2019
- Managed Security Service – MSSP - October 23, 2019
- DDoS Attacks – An In-Depth Guide - September 12, 2019









Comments are closed.