In 2007, one of the most expensive security systems in the world was breached. To do this, weapons, violence or electronic devices weren’t needed. A man took 28 million dollars in diamonds from the ABM AMRO bank, based in Belgium, by being a charming person. Obviously, this kind of weapon can’t be bought.
The guy, who called himself Carlos Héctor Flomenbaum, had an Argentinian passport which had been stolen in Israel. With his new identity, he gained the employees’ confidence at the bank over a year. While he was painting himself as a successful businessman, the thief was friendly with the bank workers by giving them chocolate boxes. One day, they provided access to him the security boxes which contained gems valued at 120,000 carats. Then, it became one of the biggest robberies committed by only one person.
The moral of this story is simple: no matter which kind of technology is provided, or how expensive it is, while the human factor is operating, the system is still vulnerable.
The user is the weakest link in security
The previous chronicle is a good beginning to talk about social engineering. A set of psychological techniques and social skills which, used consciously and premeditatedly, allow data to be stolen. What a social engineer does with the information they have gathered hasn’t got limits, although that no longer belongs to social engineering. That is why, as far as the computing world is concerned, it’s possible that a social engineer would never touch a computer or access any system.
In some cases, a social engineer does not have to gain the confidence of his or her victims, or manipulate them, as he or she can obtain data by paying attention to the information which is in view of everybody. It could be a post it on a desktop, notes of a notebook, messages that appear on a mobile screen, or even looking for data in the trash (a method known as trashing). In other words, a social engineer can get data without applying any pressure on people. In these cases, we would not be talking about a scam technique, but taking advantage of carelessness.
In the previous example, it is clear that the goal of the robbery was the gems, but it also shows us that the most important asset of any company is still information. Possibly, the thief would not have known things like where the diamonds were if the employees had not given him this information. This is the main reason why businesses should invest in system protection, but also training their workers to prevent what could happen.
We should not forget that social engineering is still one of the most used techniques among cybercriminals. This is not surprising as they have earned a billion dollars in the last two years by stealing from a hundred of banks.
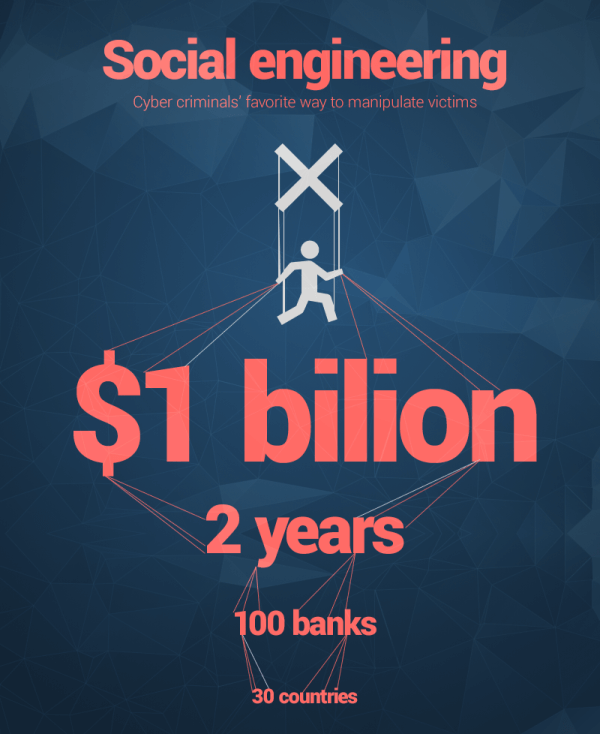
The following cases demonstrate to us how the human factor can influence a company’s profits, and also, how it could affect the state of the main markets. You will see two examples that are worth bearing in mind when a company decides to invest in improving its computer security.
Ubiquiti Networks case and reverse social engineering
The Ubiquiti Networks is an American service provider of high-performance networks for businesses. In 2015 it was hit by a cyberattack that made it lose 39.1 million dollars. For that purpose, cybercriminals wrote some e-mails introducing themselves as executive members of the company. They asked some employees of the financial area to transfer big amounts of money to a particular bank account which was controlled by the cybercriminals.
This social engineering technique takes advantage of certain human being’s weaknesses, like being helpful, since this could be recognized by superiors. Also, there are a lot of people who are incapable of refusing to do something that, thought about coldly, could be harmful.
No one entered into the computer systems of the Ubiquiti Networks and no data was stolen. In this case, the security breach was the employees, they lacked cybersecurity training, and they were unaware of the necessary procedures to face these kinds of frauds.
The influence of a fake tweet in the world economy
There are people who probably have forgot the next case. In April 2013 the Associated Press Twitter account published a tweet which damaged the world economy for a short time:
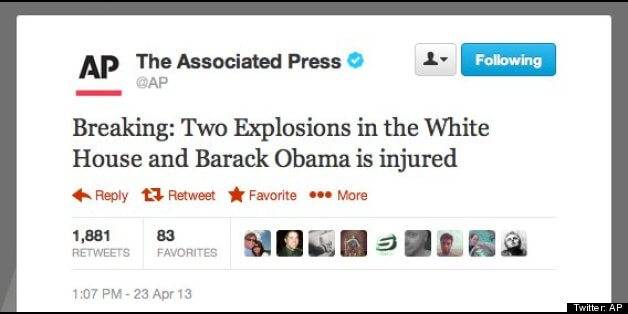
At that time, the social network didn’t have double-factor authentication for logging on. The Syrian Electronic Army, the group who claimed responsibility for the attack, took the Twitter account by sending a phishing e-mail to some members of the Associated Press. Someone took the bait and gave the login information to the hackers. In the next image, you will see the phishing e-mail which was sent to Associated Press:
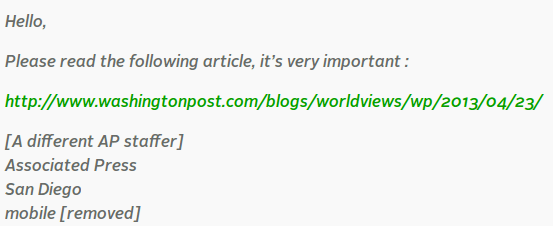
The outcome is well known: the White House denied the tweet, and the Associated Press account was temporally suspended until the staff members restored control. The markets soon recovered their original levels.
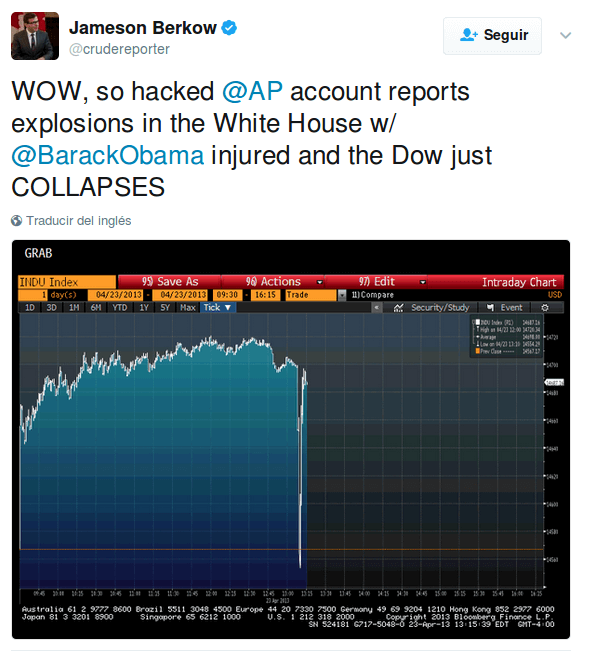
This situation shows us how weak we are facing this kind of cyberattack, and as a consequence, how vulnerable companies and organizations of any size are. This time it was the Associated Press, but tomorrow it may be any business or institution that could send harmful messages by social networks that could damage their reputation, and hence, their customer and investors confidence.
The relevance of taking action and reporting
In a TED Talks, the vice president at IBM Security, Caleb Barlow urges companies all over the world to fight against cybercrime in the same way action protocols are performed in a public health crisis. As we have seen in the 2009 flu pandemic and the Zika virus, governments and organizations of every country shared information instantly about the number of people affected and how these viruses were spreading.
This pathway is opposite of what is being done today in relation to computer attacks. Taking a look at the number of daily cyberattacks, we don’t have enough data about how many companies have been breached. The reason is fear, this information could impact on their name and also, on their finances. “If we do not share it [information], then we are part of the problem”, says Barlow.
- The keys to get the ISO 27001 certification - November 14, 2019
- Managed Security Service – MSSP - October 23, 2019
- DDoS Attacks – An In-Depth Guide - September 12, 2019








Comments are closed.