What is well known is that Google / Bing dorks are still one of the easiest ways to detect vulnerabilities in servers and web services. I decided to make this small article and talk about what I consider one of the most effective dorks when it comes to quickly detecting potentially vulnerable servers to Remote Code Execution.
JBoss is a widely used Java Enterprise Edition application server. As is well known, Java EE-based applications often have a large corporate look. This means is very common to find enterprise management applications written in Java, such as Microsoft .NET.
One of the peculiarities of JBoss is that it provides, by default, a web-based management console that allows you to manage, configure and deploy services within the JBoss server. What is the interesting thing about this? JBoss allows you to deploy services contained in “WAR” packages directly from the web console, so that if it can be accessed from the Internet without any restriction, anyone can deploy Java services on the JBoss server.
The JBoss console is generally in the /jmx-console path. It is not common to change the name of this path, so it is easy to find open consoles with a Google search: inurl:”/jmx-console”. The service is usually found in ports frequently associated with development (8080, 8081 …), although they can also be found in ports related to production environments (80 and 443) and even in less common ports.
Practical example
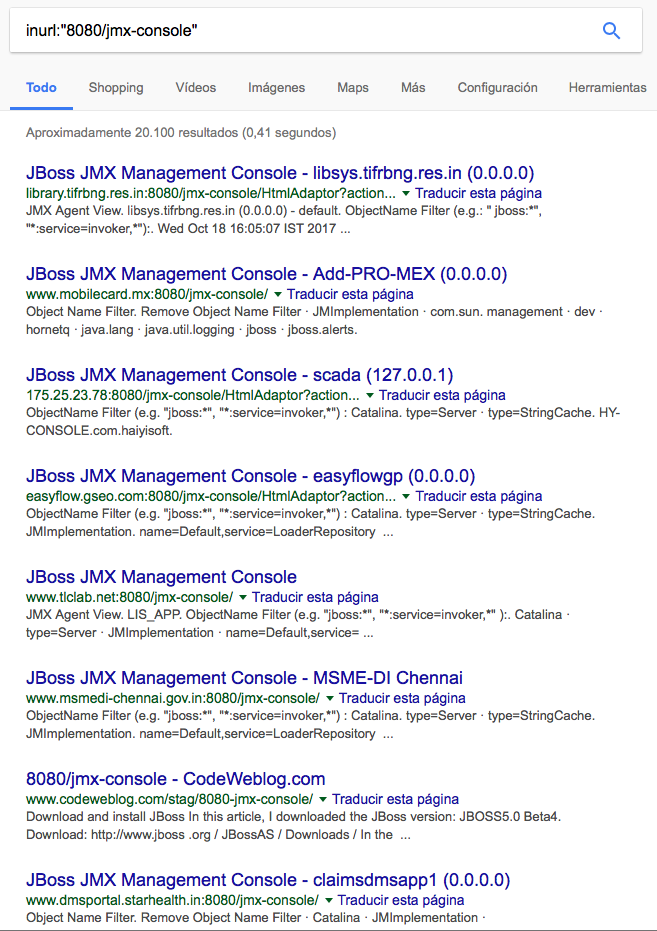
When accessing one of these consoles, we find an interface similar to the following image:
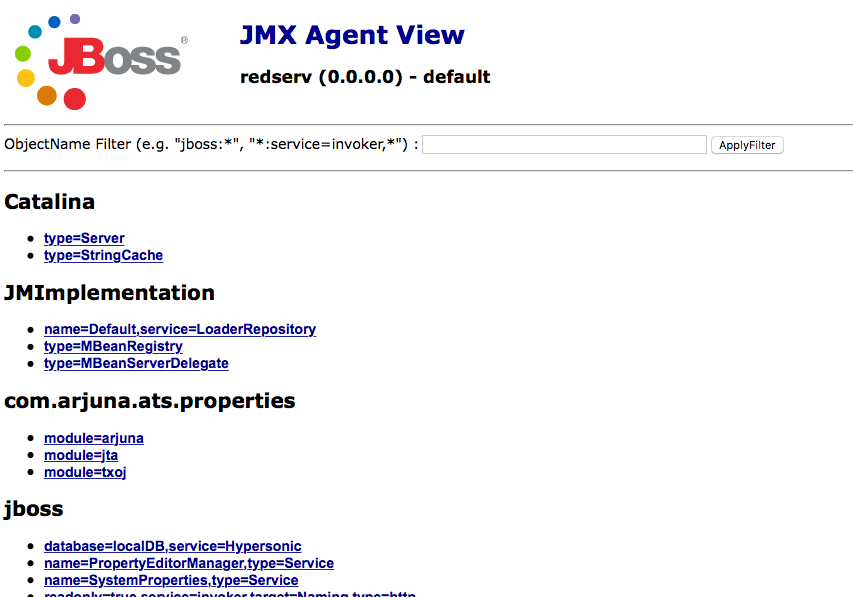
The console displays an index with all available services. We will focus on the MainDeployer service, although the ServerInfo service may also be interesting.
The ServerInfo service displays information about the server architecture and the operating system on which the JVM runs.
The MainDeployer JBoss service allows you to deploy a .war container. The most dangerous thing about this is the fact that it will accept a URL as source of the .war container and it will download it into its source path.


What happens if the container we pass through parameters is in a server we control and whose purpose is to deploy a JSP that accepts by POST or GET parameters, commands that will later be executed in the system?
Bad news. It is possible to execute remote code on the server. In the case of the previous image (a fictitious case in a local environment as a demonstration), control is obtained as a root user on the server. As a reader, if your profile is not technical, this basically means total and absolute control over the vulnerable server.
By automating JBoss consoles searches and performing some scrapping, more than 200 vulnerable different servers can be found after a few seconds. Interesting, isn’t it?
- Hacking systems running JBoss JMX Console with Google & Bing - October 23, 2017








Comments are closed.