Nowadays, users can’t trust in the things they find on the Internet because there are people who create all kinds of content which may be unproven information or incomplete. In fact, this is what you find when you search about VPN on Google. You will see results about what this service is and the benefits of using it.
Therefore, you may wonder, are VPNs that good? Is there any disadvantage? How do VPNs’ companies work when they provide their services for free? Is this service suitable for your business? Let’s see.
What are VPNS?
With the VPNs’ technology, you can create a connection between a private network or devices through the Internet. This service became a must for employees who work outside their office, as they can log onto their systems as if they were physically in the office. That is why the acronym VPN means Virtual Private Network.
Generally, your device connects to the Internet through a router (smartphones have their own), and with an IP assigned, the router sets a connection with the Internet service provider. This is the way you have access to the Internet. However, when using a VPN, your device will set communication with your VPN’s server, and then it will make a call to the Internet service provider.
Those who want to mask their IP address work with VPNs to skip the lock in countries like China, so they can get access to some content and services on the Internet. China is a good example of this, as lots of small and medium-sized companies work with services from Google like Gmail which are censored by their government.
So, these companies try to skip the censorship by using VPNs which fake their location. It is important to know that to take advantage of faking location, the VPN’s server should be in a country where there are not locks.
However, it is more common to find companies which work with VPNs to set secure connections among their employees who are outside the office and need to enter onto its systems. Theoretically, thanks to VPNs, the systems have their access protected and their connection encrypted, but now you are going to discover why this technology is not 100% secure and infallible.
What they say vs. The reality of using VPNs
Mainstream media highlight the supposed virtues of VPNs over the security problems they often report. So, we thought that the best way to evaluate this service is by discussing what media say and what happens in reality.
What they say |
The reality |
| VPNs are easy to use | If your VPN is set wrong, then it becomes a vulnerability. For example, its password may be easy to discover for hackers. |
| You can fake your location | Not in all cases, as hackers can know your mobile location without knowing its IP address. |
| VPNs encrypt data | Data encryption is very common among VPNs, but their security depends on their connection protocol. For example, PPTP protocol created by Microsoft was harshly criticised because of its unsafeness. |
| VPNs allow you to work remotely in a safe way | At the expense of your productivity. Depending on how far your VPN’s servers are, you will experience slower data transmission. It also happens because of the encryption and decryption data. Moreover, upstream and downstream speeds may be limited. |
| VPN provides you with anonymity | This is false, and it is a belief widely spread on the Internet. When using a VPN, your data won’t arrive at your Internet service provider, but at your VPN’s Internet service provider. So, if you don’t trust your VPN company, it is better not to use it. |
| There are VPNs for free | It is recommended to avoid them, as the majority of these free services don’t have functions like encrypted data. Some of the companies which offer free VPN sell users’ information to third parties like VPN Defender. |

The Private Policy of the VPN Defender’s website, says that they can share their users’ information with third parties and affiliates. That is why it is important to read the terms and conditions of the Internet’s services carefully, especially, if the security of a business depends on these services.
The Hola Case
Hola is a business based in Israel which provides to users a VPN service for free. This service works with a P2P network (peer-to-peer), in other words, it sets a computer’s network which performs as clients and servers at the same time.
In 2015, some media published that Hola was selling the bandwidth of their users to third parties. Luminati was another business of Hola who was taking the bandwidth of Hola’s users to sell it for 5 dollars. It means that Hola’s users became providers of the bandwidth of Luminati’s clients. However, this situation is explained on Hola’s FAQs:
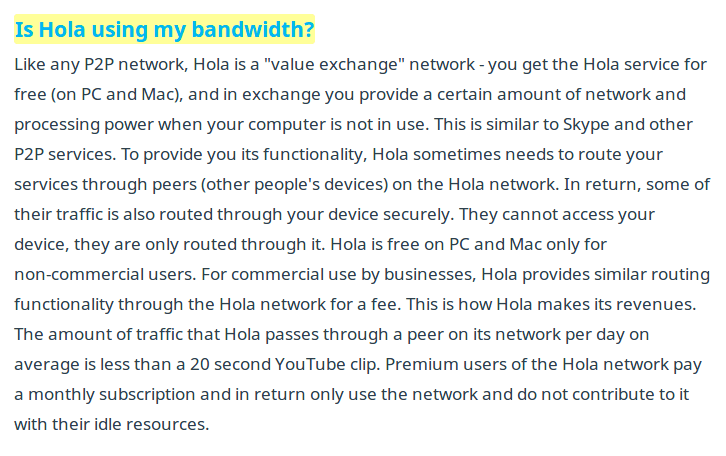
Hola’s website explains that its service consists of an exchange network.
Hola’s problems arrived when some people used Luminati’s service for addressing a DoS attack on 8chan website. Since then, Hola got bad press and this site, called “Adiós Hola”, showed why users should not trust this service.
The case of Hola, Luminati and VPN Defender are examples which show how recommended it is not to do it on the cheap. Moreover, if you have a business, you need to choose which tools you are going to trust.
Virtual Private Networks vs. Secure Access
VPNs became popular tools among businesses, especially businesses which have employees working outside the office. But, there are companies which had spent their resources in implementing these tools which are not suitable for their needs.
At this point, businesses need tools which do not sacrifice time, money and workflow, but also, these tools should provide security in data transfer without small print.
Secure Access responds to these needs. It is a unified authentication proxy we provide that gives you complete internet access without any compromise in network security or speed. You won’t need to hire a professional to set up the proxy, as Secure Access is a secure cloud service that minimises the time and money spent on setting up your security measures.
If you are a business owner who wants your company to have maximum security, whether you have workers in the office, out of office or digital nomads out there, you deserve to have the best network security, optimum internet speed, and maximum flexibility for your brand. Don’t hesitate to contact us about Secure Access.
- The keys to get the ISO 27001 certification - November 14, 2019
- Managed Security Service – MSSP - October 23, 2019
- DDoS Attacks – An In-Depth Guide - September 12, 2019








Comments are closed.