Logging onto any of your social networks or services on the Internet; putting the correct username and password and finding access denied because someone has changed your key is the beginning of a nightmare that no-one wants to live. Your account has been hacked and your digital identity can be ruined in a blink.
Unfortunately, this situation is very common. We have an intense digital life and we too often forget the importance of digital security, something that every one of us should worry about without excuse. Although 100% security does not exist, it is within our reach to put basic security measures in place to avoid such situations as much as possible.
All users are exposed to third parties who try to access personal accounts. It is time to forget the excuse “If I am nobody. Who will want to access my networks?”. Cyber criminals find it easy to hack us because of our carelessness, naivety, sloppiness, lack of interest or knowledge.
If any email account or profile of a social network has a value in the black market, it is obvious to say that any account which belongs to a celebrity with a legion of followers has more value. This turns the accounts of celebrities into an object of greater desire.
What intentions are hidden behind the hacking of celebrity accounts?
There is not a single explanation for celebrity accounts to be at the center of the bull’s-eye. Saying that behind attacks, there are cyber criminals who do it for money would be to simplify it very much. However, we could talk about three hidden intentions:
- Economic reasons. Sometimes the goal is hacking the victim to request a payment in exchange for returning the account. In other occasions, it is done to sell your data on the black market, such as emails or telephone numbers to the highest bidder or to obtain an economic benefit by selling intimate images, screenshots from private conversations or confidential information.
- Social recognition. Sometimes the hacks to celebrities accounts are carried out by fans who look for protagonism to obtain the ephemeral glory of their feat or get the attention of that famous person they idolize.
- Give a lesson in security. It may seem curious but there are groups of people who claim security measures after hacking celebrities accounts. They enter into the account of a celebrity, influencer or youtuber, show them with facts how easy it can be to access their accounts, explain what measures they must take to maximize their security and after the lesson, they return their accounts.
It should be clarified that in all these cases we are talking about a cyber crime, as intruders are breaking the law with all the consequences that entails.
Another danger of hacking social networks of recognized people is that attackers can use the account to send any message instantly to thousands, to millions of followers and this can have unpredictable consequences. Without going any further Justin Bieber’s Twitter account was hacked by the terrorist group ISIS to spread a jihadi propaganda video reaching its millions of followers.
But what would happen if instead of using the account to spread false information or upload any type of video, it will be used to spread malware? No doubt the consequences would be very serious. This hypothesis has been shared by security specialist Francisco Ramírez in some of his talks (in Spanish), using as an example the person who accumulates more followers on Twitter than anyone in the world: Katy Perry. It sounds disturbing to think that someone could hack into your account with 110 million followers and take advantage of the situation to post a tweet with a malicious link and spread some type of malware.
Basic measures of digital security to avoid the worst scenario
It is clear then that any user should work with the issue of cyber security and if the person is famous, the social responsibility to do so increases. Users must have time to adopt different security measures that can help us not to have to face to improper access to our accounts. Let’s review the most important ones:
-
- Use strong and different passwords for each of your accounts. If you use the same passwords or you set your accounts with two or three passwords for everything, then it will be easy to access for attackers. Here is a video (in Spanish) from OSI, the Internet Security Office, on how to generate strong passwords.
- Set the verification in two steps in all the services you use. All social networks allow it so you have no excuse. You must go to the security / privacy section of your Twitter, Instagram, Facebook, LinkedIn accounts or your Google profile and activate there the two step verification to match your mobile phone with your account. In this way, when you try to access, in addition to knowing the user and password, you will need to enter the one-time code that will be sent to your phone. It will be more difficult for intruders who can find out your passwords, to also have access to your device mobile in real time.
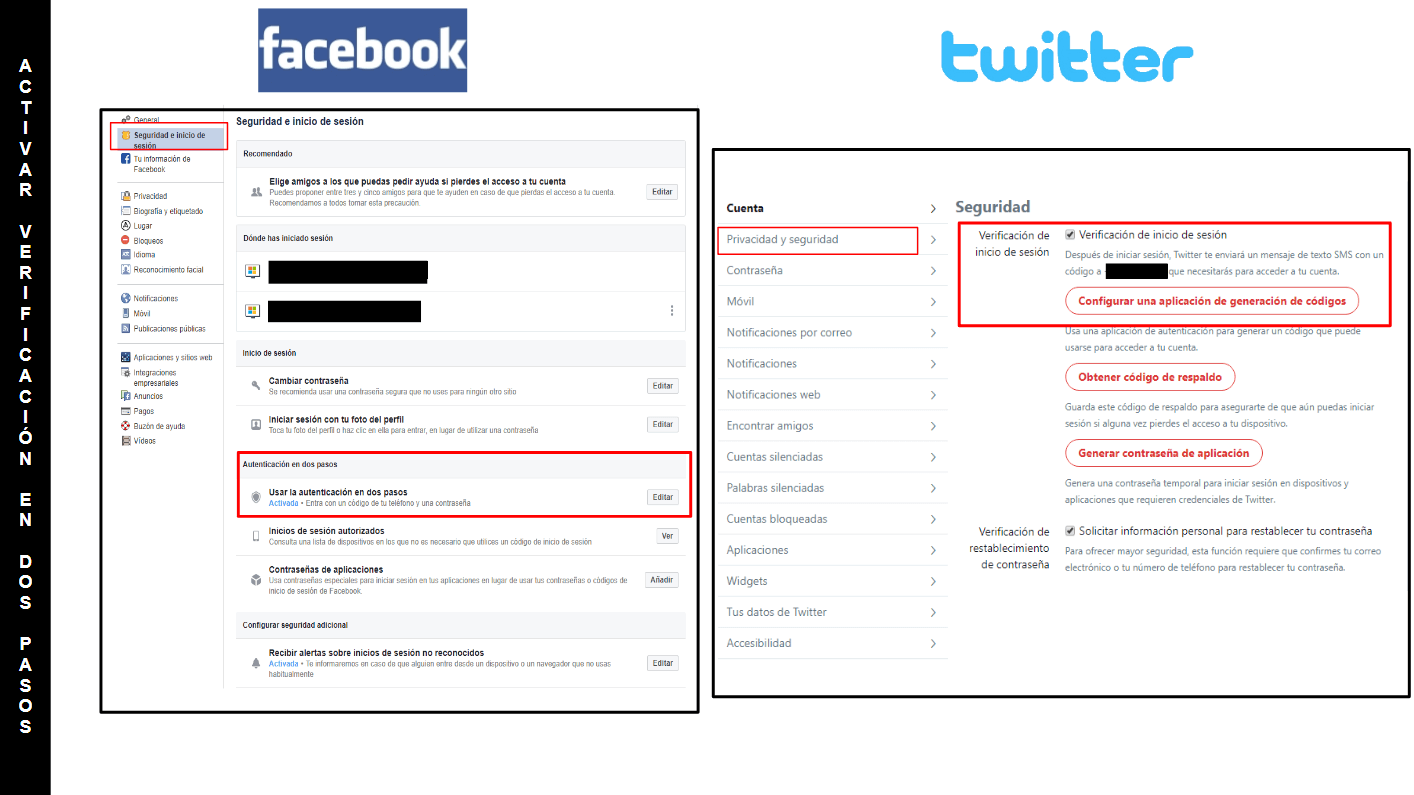
These screenshots show you where you can activate the verification in two steps on Facebook and Twitter.
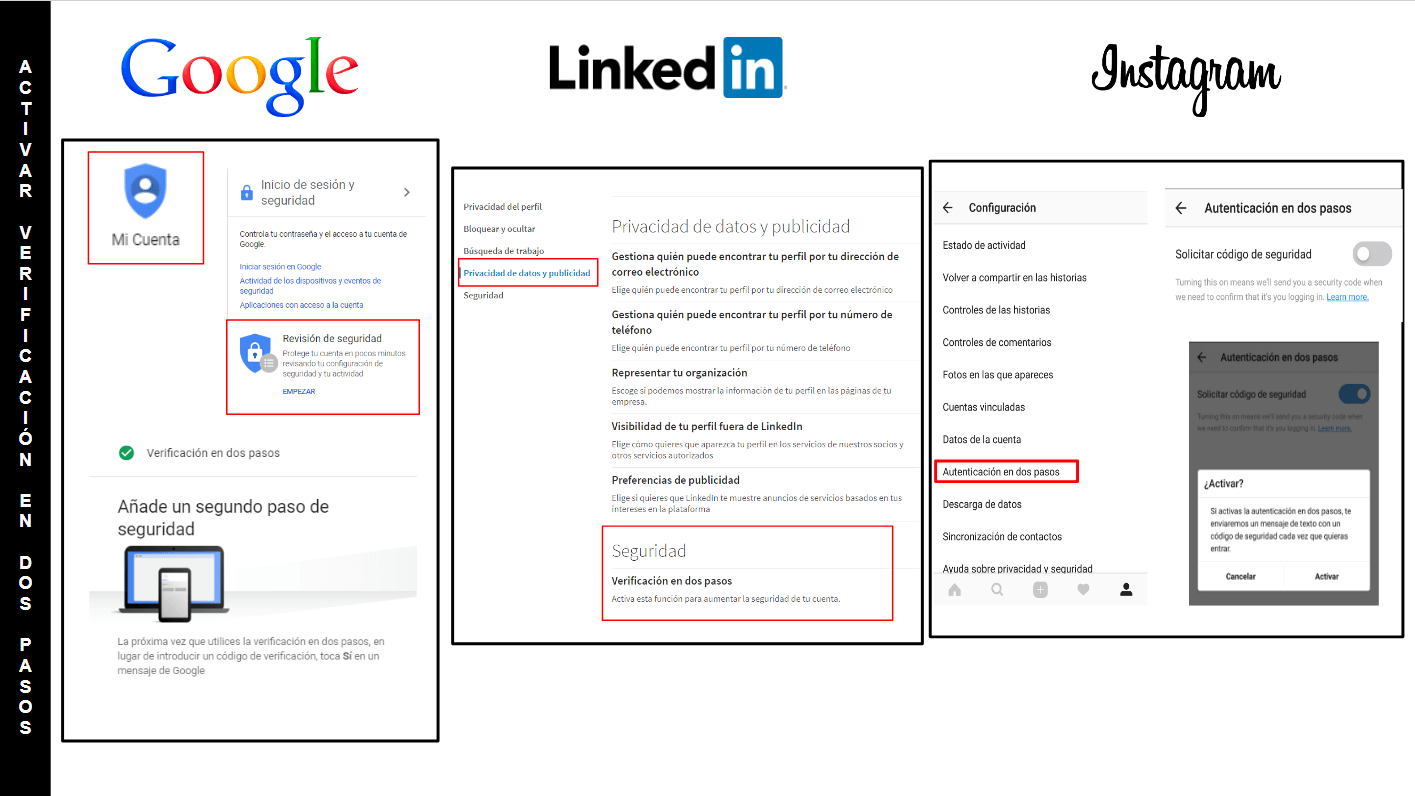
You can also activate the double authentication factor in Google services, as well as LinkedIn and Instagram.
- Check all the applications / games to which you have given permission in your social networks and remove the access to those that you don’t use. In many cases, the access door for account intrusions occurs through these applications, taking advantage of a security breach.
- Anyone from social networks will never ask for your passwords. If you receive an email to change / verify your password never do so through the possible form that you receive or through any link containing such email. It is easy to be a victim of phishing. If you want to change your password, go directly to the social network and do it from there.
- Pay attention to all the links before clicking. In many cases, cyber criminals take advantage of the shortened links or change some character of the link for another that visually seems the same but leads to an illegitimate site. Clicking there may be the entry of a virus, Trojan or spyware into your devices and provides them with the gateway to your accounts. Here you have a video (in Spanish) to see the dangers that QR codes and shortened URLs.
- Install an antivirus and other antimalware tools on your devices. Those tools will act as a barrier to avoid malicious content and don’t forget to cover the webcam of all devices connected to the Internet.
What to do if they hack any of your accounts
If in spite of adopting these basic security measures and applying common sense in your activity in social networks, you are the victim of an improper access to your accounts, the first thing you should do is stay calm.
In the slightest doubt that this has happened try to access your account first and change the password through the social network or the email associated with it. If this is not possible, try to get in touch directly with the help center to communicate what happened and try to recover your account (in the case of verified accounts, the process is simplified).
The complaint that can be filed with the police is always welcome, but I tell you that it is quite complicated to be able to reverse the situation, recover the account and find the culprit.
Sometimes none of these steps will work because the person who accesses will quickly apply in the hacked account all those security steps that I have recommended (change the email associated with the account, change the password and put a strong one, associate a phone with the account …) and that could have helped you avoid living such an unpleasant situation in which your privacy is violated, and identity usurped.
So before you have to say goodbye to a profile in a social network and resign yourself to a situation like that, what if we start worrying about our digital security first? Remember: security starts with oneself.

Guest author on the Open Data Security’s blog
- How to protect your accounts to avoid being hacked - June 13, 2018







Comments are closed.