These days we are receiving calls from people who are being infected by a ransomware called Crysis, which seems to be a continuation of the manual infections campaign using weakly protected Remote Desktop Protocol access, campaigns which were previously reported in 2016 and 2017.
The ransomware has different variants, this one in particular being identified by the .java extension of the infected files. The infections that we have presented were caused by manually infecting the victim PCs through Remote Desktop Protocol (RDP) access, which means that a human attacker is accessing the victim machines prior to the infection by bruteforcing the Windows RDP protocol on port 3389. This exploits weak credentials in order to takeover the machine´s console and desktop.
The attacker usually downloads and installs monitoring programs like keyloggers to collect data from the system and also to gather data of the activities and data of the victim. This may be a private individual or a company. Through monitoring and credentials harvesting they can also extend the scope of the attack to other resources of the victim´s network. After enough data has been collected, the Crysis variant is executed on the victim machine and the ransomware encrypts almost every file of the affected machine including executable files. This is not common in other ransomware cases.
After the files are encrypted, a text message is left in every folder of the victim´s machine that asks the victim to contact the attacker at the supplied e-mail address. The address is also present in the infected files names.
What is also uncommon considering the latest big scale ransomware attacks is the fact that the quantity of the ransom demanded by the attackers is customized in accordance to the data that the attacker obtained previously from the monitoring of the victim. A wealthier company is asked for more money than a smaller one or a private individual. Unlike previous ransomware attacks where the ransom was quantified in hundreds of dollars, these ransom demands usually reach thousands of dollars.
Unlike previous variants whose keys are already published and whose infected files can be decrypted by various tools including Kaspersky Rakhni Decryptor and AVG Crysis decryptor, this Crysis.java variant uses new, custom RSA keys, rendering the recovery of the infected files IMPOSSIBLE at the moment.
An investigation, has placed the United Kingdom in the list of the top 5 countries most affected by this type of ransomware:
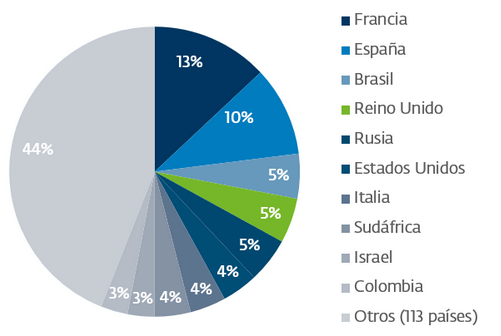
Source: welivesecurity
In recent cases we have seen that Crysis lays dormant in the affected computer for months, until the ransomware goes “into action”. In one of the cases our analysts found proof that the victim servers were used for cryptocoin mining prior to the manual infection and the ransom demand.
So, what can we do?
- Have your backups up to date.
- DO NOT click on dubious-looking links that come from emails, messages, or social networks.
- In case you get infected, DO NOT REBOOT THE MACHINE. Call a data security company immediately.
- Have a phone close to you, and call for HELP, in case the worst scenario happens.
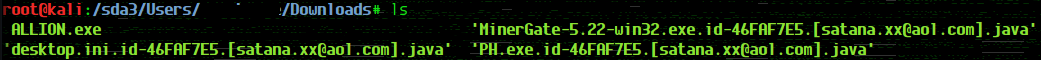
ALLION.exe – the ransomware sample, a bitcoin miner and a monitoring software found in one of the victim servers. The miner and the PH file were also infected and the name format assigned to the infected files is particular to the Crysis ransomware.
- Crysis, a dangerous ransomware that is infecting companies right now - January 10, 2018
- How to protect your business from brute-forcing subdomains attacks - June 13, 2017
- Hackers, from technological evolution pillars to governmental weapons - January 3, 2017







Comments are closed.