Nowadays, businesses have to face some invisible risks. Recent developments showed us that it’s time to become aware of these risks, because we need to know how dependent on technology we are, and also, how vulnerable we have become because of this dependency.
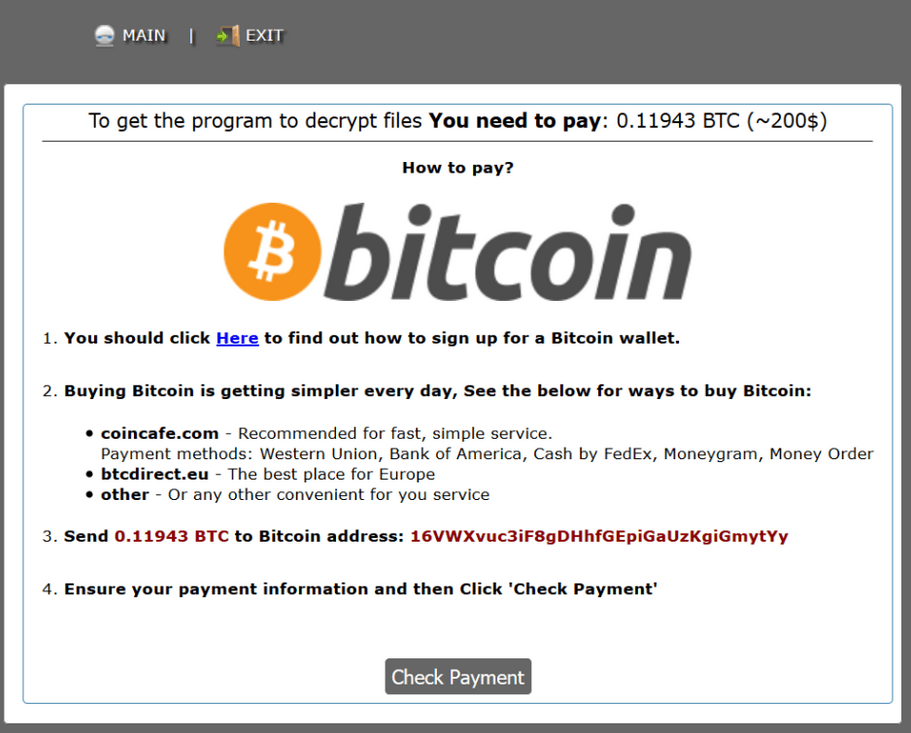
On May 12th, a virus infected hundreds of big and medium-sized companies all over the world. That morning, hackers caused panic and spread fear while mass media were confirming victims. The word “Ransomware” was the most repeated that day. It is a malware which accesses your device, encrypts the files and blocks the system until you pay a ransom. Cybercriminals want you to pay with Bitcoins, a kind of virtual money which is difficult to track.
For this attack, hackers developed a worm called WannaCry or Wcry, a variant of the WannaCrypt0r 2.0. Also, the amount of money they asked for was between 300 and 600 dollars.
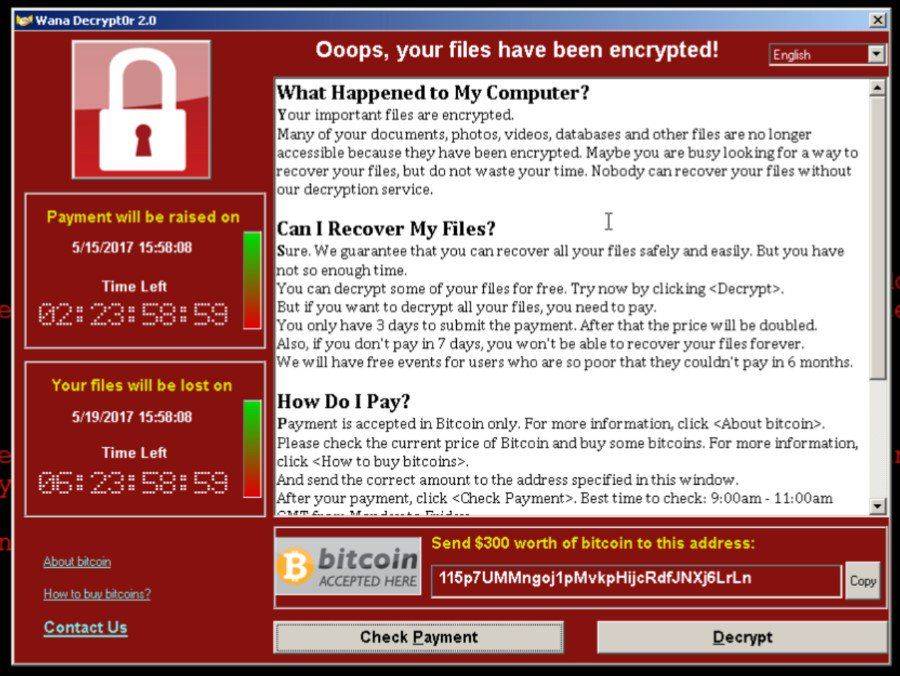
As we have seen in this post about how ransomware affects businesses, there is no guarantee that hackers are going to decrypt your files once you have paid. However, there were people who paid the ransom, as they didn’t know how to solve this situation.
How did the virus come up?
There are lots of suppositions about the biggest cyberattack of this year, but probably, many questions will go unanswered. On one side, nobody is held responsible for this ransomware attack. Sources at The Guardian aimed at a North Korean organisation called Lazarus Group. They say that they might be the developers of this virus. The New York Times repeated this scenario and added that the code of other attacks from North Korea were similar to this WannaCry virus.
Following this theory, other sources say that a group of hackers called Shadow Brokers published ETERNALBLUE on the Internet. It is an exploit which allegedly was developed by the NSA. The exploit was created to get into devices with Windows taking advantage of a security breach in the network protocol called Server Message Blog (SMSB). So, you can take control of machines with this exploit.
At the same time, security breaches of Windows were published by Wikileaks through a document called Vault 7. The papers revealed the methods that the CIA used to spy on devices with Windows. The intelligence services of the USA also took advantage of a vulnerability of this system operator, which not even Microsoft knew about (this kind of attack is also known as Zero-day)
All this information was useful for cybercriminals when they were developing the worm. The creators of the WannaCry virus used the exploit to access devices which were not updated, and they introduced the ransomware which infected all the systems connected to a local network. At the same time, the virus reproduced different IPs to expand through the Internet. That is why WannaCry was so virulent.
When Wikileaks published this information, Microsoft launched a security update to solve the vulnerabilities. However, 300,000 devices were infected all over the world, so the majority of users didn’t update their machines on time. This is a recent example of why it is important to update devices.
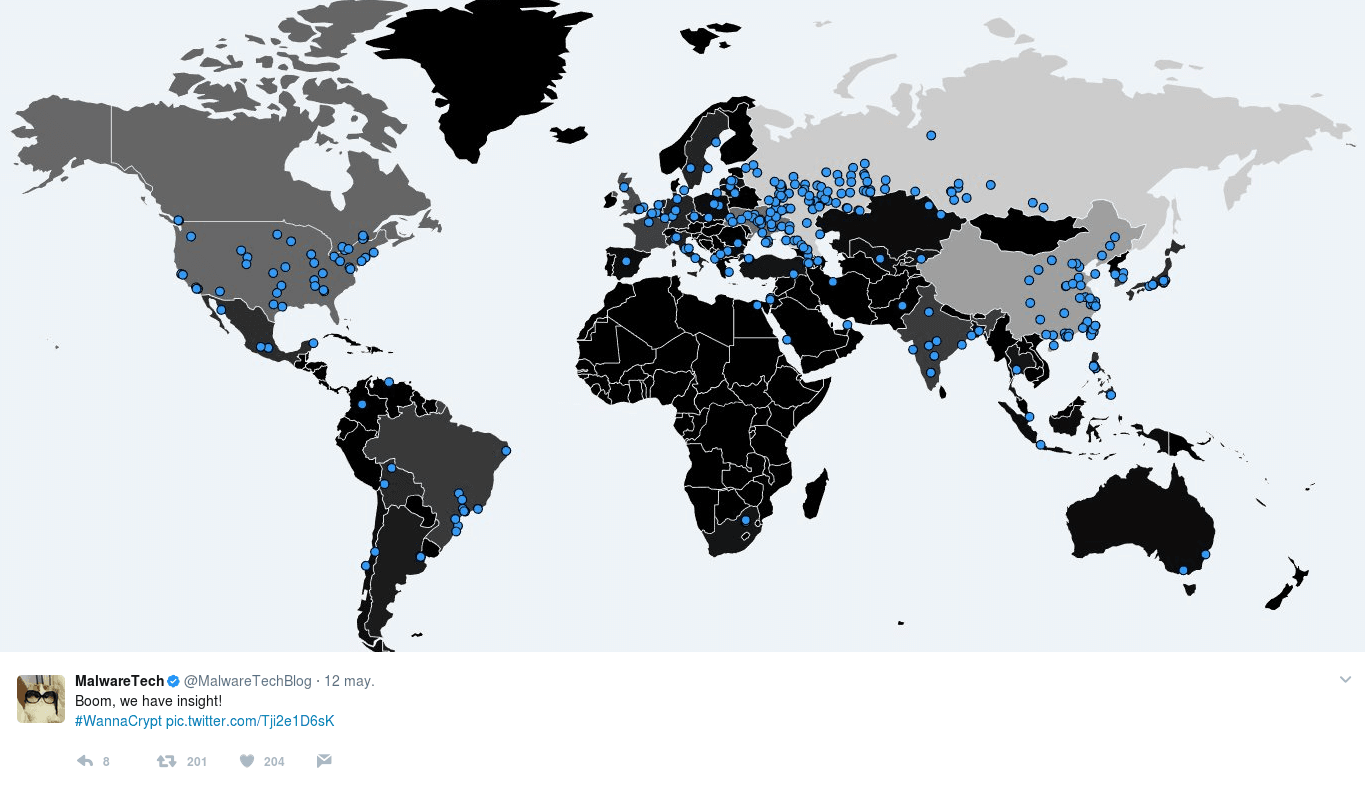
Which companies were affected?
According to Europol, more than 150 countries were infected by the WannaCry virus, among them, Russia, Ukraine, China, Spain and the United Kingdom.
In fact, the UK was one of the first countries where the alarms belled. Computers of the National Health Service (NHS) were infected by the WannaCry ransomware. Hospital staff had to delay appointments, divert ambulances and cancel surgeries if there was not any emergency.
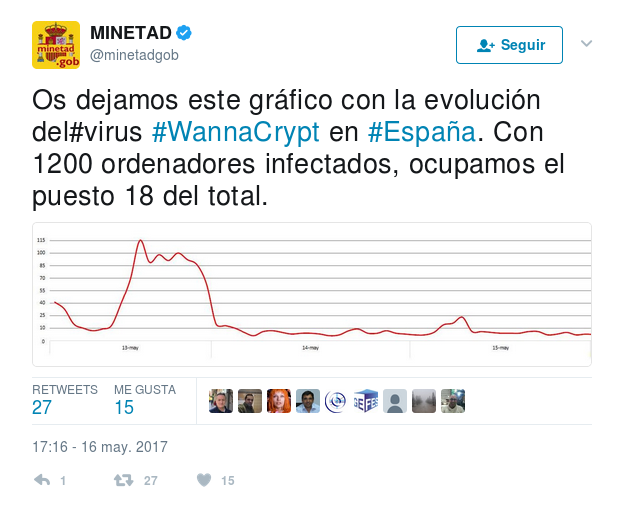
In other countries like Spain, nearly 600 companies stopped their business activity because of this attack. Telefónica was one of them. The employees of the telecommunications provider switched off their computers and disconnected from the Internet until further notice.
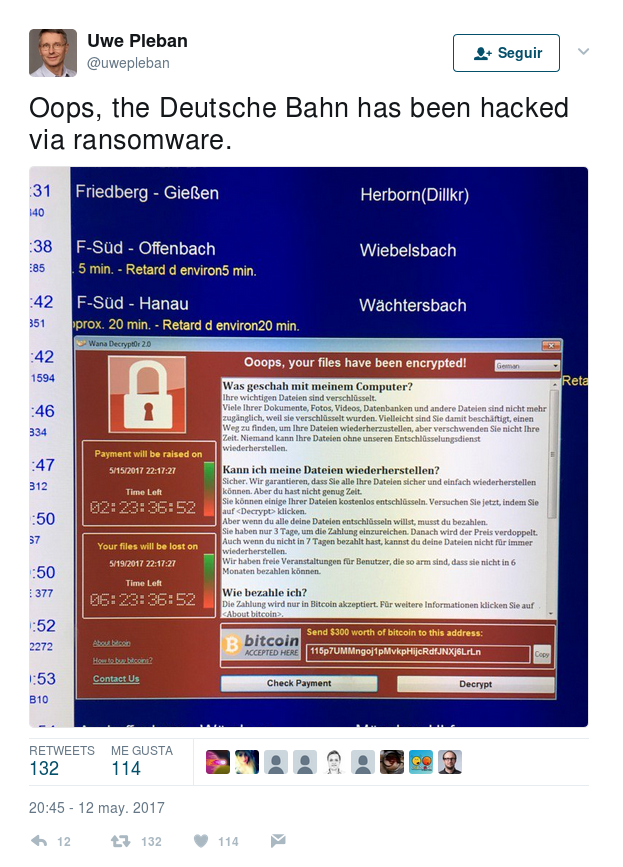
On an international scale, other companies were affected, too. Renault suspended their activity in some of their factories. The German railway operator, Deutsche Bahn, confirmed that their systems were infected, too. Some people took photos of the virus on the panels of rail stations.
How was the virus stopped?
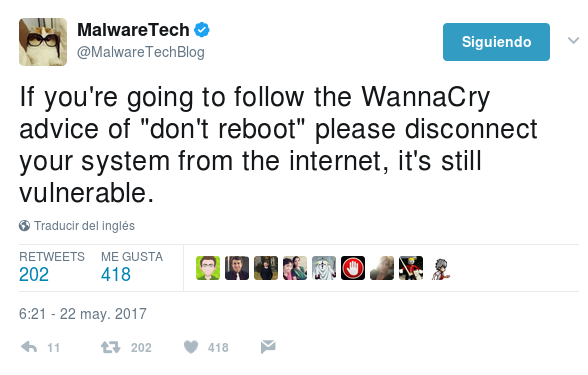
Marcus Hutchins, also known as @MalwareTechBlog, is a 22 year-old boy from Devon (England). In an interview with the Associated Press, this security expert explained that he was on holiday when he started to analyse how WannaCry infected devices. He realised that the virus was trying to call a domain name (gwea.com) every time an infection occurred.
The domain name was not registered. So, Hutchins thought that he could buy it and stop the reproduction of the virus by taking advantage of the connection between the domain name and the worm. This is also known as a “kill switch”.
He spent $10.69 to buy the domain name, and he pointed it to some servers which Hutchins had access to. When he did that, he saw the potential of the attack: WannaCry was producing 5,000 connections every second. Finally, the ransomware got into an endless loop and switched off.
Some people say that this error in the code of WannaCry was intentionally left by hackers in case they lost control of the virus. The ransomware was stopped, however several sources (among them, Europol) advise that the virus might come back stronger that it was.
Adylkuzz, Uiwix… this is just the beginning
Computer experts confirm that there are viruses more dangerous than WannaCry. Adylkuss is one of them. Hackers install the virus on computers creating a network of devices (botnet). All computers infected work for the hackers by producing criptocoins.
This activity is also known as criptocoins mining, and hackers get lots of money, as they send all the virtual money produced by the infected machines to their bank accounts. It is considered a very dangerous virus.
Uiwix, the ransomware self destructs once discovered
This is another dangerous variant of WannaCry virus. This ransomware sets up in the memory of the device, which means that it does not need to create any file. An anti-virus may find it difficult to detect it because of this. However, Uiwix is designed to self-destruct once it is discovered by the user.
In this case, the ransomware does not include a kill switch, so its code does not have errors like WannaCry. According to Heimdal Security, hackers who infect your computer with Uiwix, take control of your system, encrypt your files, and ask you to pay a ransom.
Are we ready for another cyberattack like WannaCry?
WannaCry made clear that the world was not prepared to face these kinds of attacks. On one side, it is difficult to punish cybercriminals, as attacks transcend borders. On the other side, business and individuals need to assume part of the responsibility for damage, as they are not taking the steps for their security. Moreover, this situation becomes worse with the disclosures of organisations like Wikileaks, as well as the theft of tools developed by intelligence services.
Updating devices is a security step, but it is also important to know how to face a threat. The employees of any company should know security basics, and if you are a manager of your business, then you need to know how you can shield your networks or servers. These questions can’t wait until another attack happens.
WannaCry showed us a lesson: cybersecurity is not a whim of those companies which invest in it. Protecting your company is a way of ensuring its productivity and the trust of your clients. Finally, when it comes to business issues, you need to be prepared for what is coming.
- The keys to get the ISO 27001 certification - November 14, 2019
- Managed Security Service – MSSP - October 23, 2019
- DDoS Attacks – An In-Depth Guide - September 12, 2019







Comments are closed.