When the Internet wasn’t known as Internet, but ARPANET in the 70’s, the email was already becoming popular.
However, if there is something we have known for a while, it is that all technology has a negative part that can be exploited. And it is being exploited.
In the case of emails, cyber-criminals use creative techniques to extract data or economic resources from users and companies.
In the following lines, we will identify the threats that we face when we open our inbox in a work environment and offer recommendations to avoid disaster.
Cyber threats in email
In cyber security there is a recurring phrase:
The human being is the weakest link.
In other words: a system could be equipped with the latest software for protection, but when it is managed by people, that protection may stop.
How is this possible?
It is due to phishing. It involves a series of techniques that exploit some of the weaknesses of the human being. These are:
- We all want to help.
- By default, we usually trust people.
- We don’t like to say “no”.
- We like to be praised.
Therefore, when an attack is launched through email, there are lots of successful methods that use phishing. The most common are malicious links, attachments with malware and identity theft. Let’s see each of these below.
Malicious links
Incoming emails arrive looking harmless: a sender, a subject, the body of the email and a link to click on.
The link should put you on notice, especially if the email comes from an unknown contact or it has not been requested.
Sometimes, nothing happens by clicking on the link, because the danger comes when the link leads to a fraudulent page (similar to the legitimate one), and we are asked for data that the attacker ends up obtaining.
→ Example of phishing attack in the mail
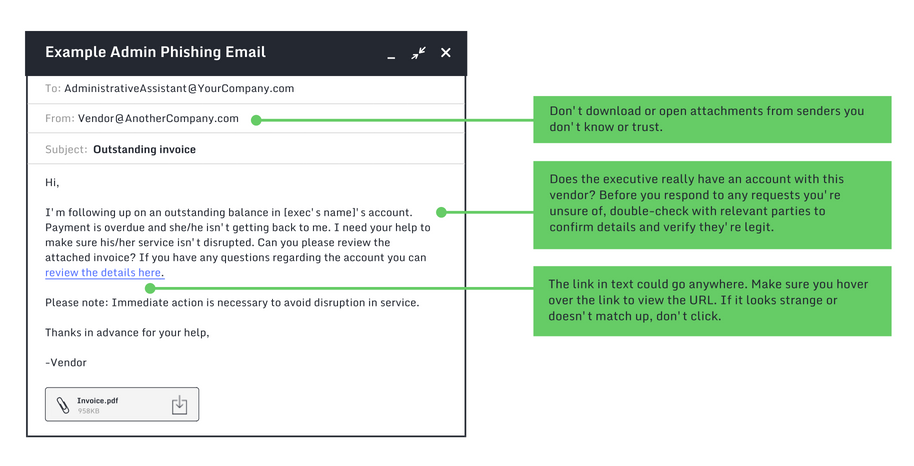
However, there are attacks in which it is enough to click on the link. There are cases when the computer becomes infected by loading a malicious page. That will depend on the type of threat you are facing.
How to react to this threat
- Before clicking on any link, analyze the content of it:
- Think: what are they asking? If it’s about sensitive or critical data such as passwords or card details, you should be suspicious.
- Ask yourself: are you talking with the legitimate person or company? Check the email address carefully to verify if the sender is the real one. If you are still suspicious, contact the entity or person by other methods.
- It’s very useful to put the cursor over the link before clicking on it to check where it takes you. If it is a shortened link, this advice doesn’t help much, since you will not be able to read the URL.
- On the Internet you can find scanners of links and files like this one. You can simply copy it (without clicking on it) and do the checking.
Attachments with malware
In the same way that emails arrive with links, it’s usual to receive them with attachments. Many times these files come from legitimate people, which means that they send the files without the intention of carrying out an attack. The problem is that many files infect without users knowing.
Updated anti-virus should detect this situation.
However, the most common scenario is one in which a sender writes an email in a way that the recipient downloads and opens it without thinking too much.
An example of this situation occurs near the end of the tax year in Spain. Attackers send a message (sometimes by other methods such as SMS, Whatsapp or Telegram) where it is reported that the Tax Agency can not return the money to the taxpayer because of a lack of information. Therefore, the victim is asked to download the attached file and fill it with sensitive data.
From the official website, they recommend taxpayers never respond to any request for confidential, financial or personal information. Therefore, they advise distrusting any communication where confidential data is requested.
Another danger of attachments are the macros of office files, such as excel files.
A macro is a series of commands that are used to automate a repetitive task. The commands are executed when the tasks have to be performed.
Having the macros enabled by default entails a series of risks, such as the fact that the computer gets compromised when an infected excel is opened.
For this reason, it is highly recommended to have the macros disabled and to enable them only in cases where we are sure of the origin of the file. Also, it is recommended to scan it with an anti-virus before opening it. From this official Microsoft Office page, they teach you how to disable macros.
How to react to this threat
- It is advisable to be wary of attachments that arrive to the inbox and those that arrive through instant messages. Always use the anti-virus for those files before opening them or make sure they come from a legitimate sender.
- Never provide sensitive data, either through an attachment or in the body itself.
Identity theft (CEO scam)
Email is a great tool that allows us to maintain a communication with our contacts from anywhere and at any time.
Its great advantage is, at the same time, a great inconvenience for the users.
Lack of interaction face to face facilitates deception. That’s what identity theft is about, making the other person believe that they are dealing with the real person or company to get something out of their own benefit, in order to access data or steal money.
Within this section, the scam of the CEO is particularly important. In recent years, it has become a major threat to companies.
The scam of the CEO consists of posing as the head of a company or simply as a superior, when sending an e-mail to a worker of the company so that they have to make an urgent payment to a client. Cyber-criminals use an email address similar to the person they are posing as and facilitates the data so that the payment is made in their bank account.
→ Example of a CEO scam
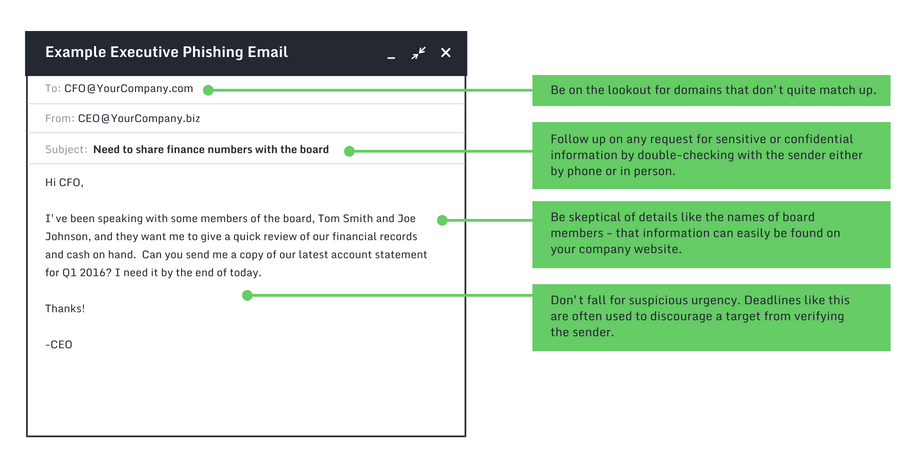
Sometimes, this scam is also done by posing as a provider of the company, so you have to be careful with the information that is given out about the activities of the organization.
How to react to this threat
For this scam it is essential to contact the person or entity, using other methods rather than the mail. It will confirm that the request is legitimate and not a scam.
Training and security policies: the essentials to defend against e-mail threats

One of the first pieces of information that any employee should know when arriving at a new job is related to training in cyber security.
This is especially important in those companies and organizations with a technological base, since the more technology involved, the more likely it is that it will suffer cyber-incidents.
Cyber security professionals recommend prioritizing training over investment in security tools and software.
Becoming familiar with the policies of security of information technologies present in the company is one of the objectives of training. There must be a document that reflects the rules and procedures that must be applied or put in place when a situation arises that concerns the security of the company.
For example, in the security policies it should be clear how to use the company’s email or what to do when detecting a cyber threat in the inbox.
Other recommended actions to conserve the integrity of the data that we have in the inbox consist of enabling the double factor of authentication or encrypting the emails that are sent between workers. All precautions are small yet important when it comes to preserving the data in the information age.
- The keys to get the ISO 27001 certification - November 14, 2019
- Managed Security Service – MSSP - October 23, 2019
- DDoS Attacks – An In-Depth Guide - September 12, 2019







Comments are closed.